Abstract— Virtual forensic investigations contain the gathering and analysis of virtual data to discover evidence of unlawful or unethical conduct. In current years, there was a big boom within the use of digital devices, consisting of smartphones, computer systems, and the internet, making them a treasured supply of information in criminal investigations and civil litigation. One area of hobby in virtual forensic investigations is the tracing of human conduct through virtual proof. This includes studying the virtual artifacts left in the back of via people in their online activities, which can offer insights into their conduct and movements. These artifacts can variety from emails and social media posts to browsing history and location information. In crook instances, virtual forensic investigations can assist identify suspects, set up timelines of events, and provide proof to help or refute an alibi. For example, studying the vicinity data from a suspect’s smartphone should help decide whether or not they had been inside the region of against the law scene at the time it took place.in addition, in civil litigation cases, virtual forensic investigations can be used to find proof of fraud, highbrow belongings robbery, or different forms of misconduct. Digital proof can also be vital in employment disputes, together with in cases of employee misconduct or facts theft. Furthermore, virtual forensic investigations can also useful resource in developing profiles of individuals, which include their on-line conduct and options.
Introduction
Digital forensics refers to the usage of specialized strategies and equipment to extract, analyze, and maintain digital proof in prison cases. [1].The use of virtual forensics has end up increasingly more established in latest years with the full-size use of technology and the growing reliance on virtual gadgets for communiqué and record maintaining. [2].Via virtual forensic investigations, human behavior can be traced and analyzed, offering valuable insights in various components of our lives. [3].Virtual forensics can be applied in an extensive range of eventualities consisting of crook investigations, corporate investigations, civil litigation, or even private disputes.[4]. In criminal investigations, digital forensics may be used to gather evidence from electronic gadgets, together with computer systems, smartphones, and other digital media, that could have been worried within the commission of a criminal offense. [5].This evidence can then be analyzed to help establish a timeline of events, perceive capacity suspects, and apprehend their conduct. [6].Further, in company investigations, digital forensics can be used to discover and prevent fraud, robbery of highbrow property, and other unlawful activities.[7]. By using reading virtual proof from organization gadgets and networks, investigators can find patterns of conduct that could suggest insider threats, unauthorized get entry to, or facts breaches. [8].This statistics may be critical in preserving the integrity and safety of an agency’s belongings.
[9].The sphere of digital forensics has revolutionized the manner wherein human behavior is traced in modern society. Virtual forensics is the practice of collecting, analyzing, and retaining digital evidence in order to investigate and hit upon crook sports. [10].This era has turn out to be critical in contemporary investigations, as maximum of human behavior happens inside the digital realm. Inside the past, traditional forensic strategies have been used to trace human behavior, together with fingerprinting and DNA analysis. But, with the arrival of era, virtual forensics has grown to be an increasing number of vital in tracing human behavior. Digital devices inclusive of computers, smartphones, and different electronic storage gadgets now contain an enormous quantity of private information and statistics that can be used to gain perception into a person’s conduct.one of the primary innovations in digital forensics is using metadata evaluation. Metadata is data stored inside virtual documents that provide information on while and how the record changed into created, modified, and accessed. By using studying the metadata of a virtual document, investigators can song the moves of a suspect and build a timeline of their movements. This lets in for a more accurate reconstruction of activities and allows in figuring out capacity suspects. Every other vital innovation in virtual forensics is the development of statistics mining techniques. Statistics mining includes extracting styles and statistics from large units of data
- Fixing Crimes: one of the fundamental contributions of digital forensic investigations is its capacity to clear up crimes. Digital forensic experts use numerous techniques and equipment to extract and analyze digital evidence such as pc files, net surfing history, and communiqué facts to piece collectively a timeline of events and become aware of capacity suspects. This could assist regulation enforcement corporations and felony authorities to accumulate incriminating evidence and construct a strong case for prosecution.
- Revealing reason: digital forensic investigations also can offer insights into a person’s reason and thought procedure. By means of analyzing someone’s virtual activities, experts can determine their conduct styles, intentions, and motives. These records may be important in understanding a wrongdoer’s moves and potentially preventing destiny crimes.
- Stopping Cyber security Threats: virtual forensic investigations are an essential tool in detecting and stopping cyber security threats. By way of reading virtual devices and networks, professionals can perceive vulnerabilities and establish proper security measures to protect in opposition to cyber-attacks. This proactive technique can help safeguard touchy records and prevent ability statistics breaches.
- Uncovering Fraud: Fraud is a widespread danger to companies and people alike. Digital forensic investigations can screen fraudulent sports thru the examination of financial information, email communications, and other virtual evidence. This will help mitigate monetary losses and keep perpetrators liable for their actions.
Related Works
The upward thrust of digital technology has notably transformed the manner people talk, devour statistics, and behavior their everyday activities. But, with the extended use of digital devices and the net, there has also been a rise in criminal activities facilitated thru that technology. So as to analyze such crimes, digital forensics has emerged as an increasing number of vital devices for regulation enforcement groups. Digital forensic investigations contain the collection, renovation, and analysis of digital proof to pick out, track, and prosecute perpetrators of cybercrimes. But, using virtual evidence in criminal investigations brings about a number issues and demanding situations, mainly on the subject of tracing human behavior. This essay will discuss the important issues in diagnostic fashions for tracing human conduct through digital forensic investigations.one of the most important challenges in tracing human conduct through digital forensic investigations is the continuously changing landscape of era. As new technology are evolved and existing ones are up to date, it becomes more and more tough to keep up with the techniques and tools used by criminals to dedicate digital crimes. This makes it challenging for forensic investigators to appropriately pick out and analyze relevant digital evidence, and might result in errors that might jeopardize the research or prevent the prosecution of perpetrators. Every other principal trouble in diagnostic models for tracing human behavior through virtual forensic investigations is the lack of standardization and consistency the emergence of the digital age has converted the way we stay, paintings, and have interaction with each other. It has additionally given upward push to new varieties of crime, which necessitates the want for powerful virtual forensic investigations. These investigations are critical in tracing human conduct and figuring out motives behind criminal sports. In latest years, computational fashions were evolved to enhance the performance and accuracy of digital forensic investigations. on this essay, we will speak the latest computational fashions for tracing human behavior thru digital forensic investigations and their effect on the field.one of the most widely used computational fashions in digital forensic investigations is the Suspect-oriented Behavioral analysis (SOBA) model. This version combines theories of criminology, psychology, and pc science to identify styles of conduct, motivations, and relationships of suspects in a cybercrime. It makes use of facts mining and gadget learning strategies to research numerous varieties of virtual proof, which includes social media activity, emails, and browsing history, to create a profile of the suspect. This profile presents investigators with valuable insights into the suspect’s behavior, which can be used to similarly the research. Every other critical computational version is the Cyber-criminal Social community analysis (C-SNA) model. The novelty of tracing human behavior via virtual forensic investigations lies in the use of virtual proof to uncover and analyze patterns and trends in human conduct. This approach allows for a deeper understanding of someone’s actions, intentions, and motivations, and may provide precious insights into their selection-making technique. Traditionally, understanding and studying human conduct has relied on strategies which include surveys, interviews, and observations. Whilst those techniques can be beneficial, they’re restricted of their ability to offer a complete and correct photo of a person’s conduct. This is wherein virtual forensic investigations are available. Digital forensic investigations contain the gathering, protection, and evaluation of virtual evidence from diverse resources which include computer systems, cellular devices, and on line systems. This evidence can consist of emails, chat logs, browsing records, social media hobby, and extra. Via analyzing this virtual evidence, investigators can hint someone’s on-line sports and interactions, presenting a greater complete understanding of their behavior. One key aspect of tracing human conduct via virtual forensic investigations is the capacity to track and analyze conduct over time. This could reveal styles and traits that won’t be apparent through conventional techniques of analyzing behavior. For example, by examining someone’s on-line activity over a period of weeks or months, an investigator can be able to pick out changes.
Proposed Model
Virtual forensic investigations contain the collection, analysis, and renovation of statistics from digital devices and networks. This includes facts such as documents, documents, emails, internet surfing history, social media hobby, and metadata. Thru superior forensic techniques and equipment, investigators can reconstruct a timeline of a person’s sports and behavior, providing precious insights into their virtual footprint. One method typically utilized in virtual forensics is timeline analysis.
This involves examining machine logs and timestamps to create a chronological timeline of occasions and actions taken on a device or network. This will help investigators recognize while and how someone accessed and interacted with virtual statistics, presenting clues approximately their behavior. Another critical factor of virtual forensics is data carving. This includes improving deleted or hidden statistics from a device using specialized tools and techniques. This may be especially beneficial in tracing someone’s virtual conduct as it can uncover important records that might have otherwise been misplaced. Metadata analysis is another key approach used in virtual forensics investigations. Metadata is facts this is stored with a file or piece of facts, offering info which include advent date, creator, and location. With the aid of analyzing this metadata, investigators can advantage insights into while, in which, and by way of whom a bit of digital facts changed into created or modified.
Construction
Creation: the development of a virtual forensic research includes multiple technical aspects that assist trace human conduct. That technical information can be divided into three important classes – records acquisition, records analysis, and information interpretation. Fig 1:Shows Behavioral digital Forensics version
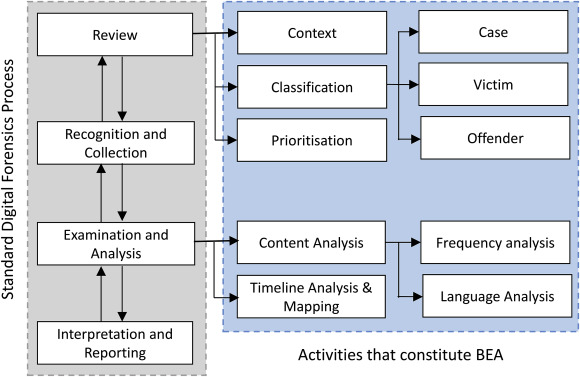
Fig 1: Behavioral digital Forensics version
- Facts Acquisition: This entails the collection and renovation of digital evidence from diverse devices and assets. This can include computer systems, smartphones, tablets, wearable devices, and internet-related gadgets along with safety cameras and smart home gadgets. The data may be received via special strategies inclusive of imaging the device, extracting information from cloud storage, or reading network visitors.
- Information analysis: as soon as the data has been acquired, it wishes to be analyzed to apprehend the conduct of the character. This entails the use of various forensic equipment and techniques to extract relevant facts, such as text messages, name logs, social media hobby, browsing history, and app utilization. It additionally entails figuring out timestamps, relocation records, and different metadata which could provide insights into the character’s moves.
- Statistics Interpretation: After the statistics has been analyzed, it needs to be interpreted to make sense of the facts accrued. This includes correlating special portions of evidence to create a timeline of events and knowledge the context of the movements. It also involves identifying patterns, trends, and anomalies in the records that may offer
Operating Principle
The running principle of virtual forensic investigations entails the collection,
preservation, evaluation, and reporting of digital proof so that you can trace human behavior. Fig 2:Shows Unboxing the digital forensic investigation technique
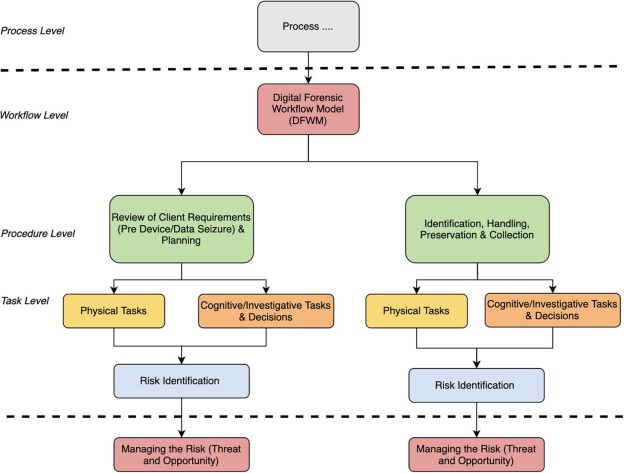
Fig 2: Unboxing the digital forensic investigation technique
- Collection: step one in a digital forensic research is to gather all relevant virtual evidence. This could include digital gadgets inclusive of computers, smartphones, tablets, and outside hard drives. The investigator need to ensure that all devices are treated cautiously to avoid negative or changing the evidence. They may also make word of bodily indicators on the devices, together with stickers or scratches, which can offer precious insights into the use of the device.
- Renovation: once the proof is accumulated, it ought to be preserved in a relaxed and managed environment to prevent any tampering or alteration. This could involve creating a forensic photo of the facts that is a precise replica of the authentic proof. The investigator ought to additionally make certain that right chain-of-custody strategies are followed to hold the integrity of the proof.
- Analysis: the next step is to analyze the accrued proof to discover any relevant statistics. This could consist of analyzing documents, internet records, emails, social media pastime, and other virtual artifacts. The investigator will use specialized equipment and strategies to extract information and pick out styles or anomalies that may be relevant to the research.
Functional Working
The procedure of tracing human conduct via digital forensic investigations includes reading and gathering evidence from diverse virtual devices and structures to understand the sports and conduct of someone.
The first step in a digital forensic research is to acquire and hold the information that can potentially comprise proof of a man or woman’s conduct. This includes seizing and copying data from gadgets which include computer systems, cell phones, pills, and different digital garage media.as soon as the facts is collected, the following step is to extract the applicable information that might doubtlessly monitor the behavior of the man or woman. This entails the usage of specialized tools and techniques to extract facts from numerous digital gadgets, applications, and networks. The extracted records are then analyzed to pick out and interpret patterns, relationships, and anomalies.
This could include examining text messages, emails, social media hobby, net browsing records, and different digital footprints to advantage insights into the character’s conduct.in addition to studying the content material of the records; virtual forensics also involves inspecting metadata, which provides statistics about the creation, amendment, and usage of virtual documents. This could in addition help in understanding the behavior of a person, including their virtual conduct and interactions.
Results and Discussion
The result (real-time occasion-Detection gadget for consumer-behavior tracking) is a digital forensic investigative device designed to track and examine human conduct thru actual-time tracking of digital activities. It changed into evolved by using a team of researchers from the middle for safety statistics system (CSIS) on the University of Texas at Arlington. The device works by gathering and studying statistics from numerous virtual sources such as net surfing history, social media pastime, email conversation, and document switch. It makes use of superior algorithms and gadget studying strategies to pick out patterns and anomalies within the statistics that could indicate suspicious or malicious conduct.one of the key capabilities of the end result is its capacity to monitor person behavior in actual-time, allowing investigators to quick come across and reply to ability threats. The system also has the capability to generate signals and notifications based on predefined guidelines and thresholds, making sure that investigators are right now notified of any suspicious interest. To protect user privacy, the result utilizes encryption and anonymization techniques to ensure that personal records is not found out throughout the investigative manner. The machine also allows for consumer consent and manipulate, allowing people to decide-out of tracking if favored.in addition to tracking ability threats, the result also can be used to conduct submit-incident investigations, imparting a comprehensive analysis of consumer sports main as much as an occasion.
Recall
The don’t forget is a system in digital forensic investigations that includes the recuperation of statistics or records from a laptop gadget or digital devices. This system is commonly used to hint the human behavior, sports, and actions which have been executed at the machine or tool.
There are numerous technical elements concerned within the consider procedure that useful resource within the tracing of human behavior. Fig 3:Shows the Computation of recall
Fig 3: Computation of recall
These include:
- Record carving: this is a procedure of extracting deleted or hidden files from a storage device. When documents are deleted, they may be not completely erased from the device, but instead their hyperlinks to the record system are eliminated. Report carving strategies permit for the reconstruction of deleted files, providing precious data about person activities.
- Live evaluation: This involves the exam of a strolling machine to acquire facts about the currently active strategies, network connections, and person sessions. This enables investigators to identify any suspicious or unauthorized activities that may be taking location at the machine.
- System and alertness logs: those logs keep a document of all the activities on the system, which include user logins, program executions, community connections, and record adjustments. Analyzing these logs can offer valuable insights into user conduct and any capability safety breaches.
Accuracy
“Accuracy” refers to the degree of correctness or precision of the information and conclusions acquired via virtual forensic investigations tracing human behavior. Its miles a key degree of the reliability and validity of the evidence amassed in these investigations. There are numerous technical elements that could impact the accuracy of virtual forensic investigations, including the subsequent: Fig 4:Shows the Computation of Accuracy
Fig 4: Computation of Accuracy
- Information series: accurate records series is essential for obtaining reliable evidence. This includes ensuring that everyone applicable statistics is identified, preserved, and collected in a forensically sound manner to save you any tampering or alteration.
- Protection: The right renovation of digital evidence is essential to preserving its integrity and accuracy. This involves storing the statistics in a secure environment and preventing any unauthorized access or modifications.
- Analysis strategies: The techniques and tools used to analyze the collected information also play an enormous function in the accuracy of the research. Investigators must use well-known and tested methods to make sure the reliability and reproducibility of their findings.
- Chain of Custody: The chain of custody refers back to the monitoring of evidence from its series to its presentation in courtroom. Its miles essential to maintain an intensive and accurate chain of custody to establish that the evidence has now not been tampered with or altered.
Specficity
Specificity refers to the potential of a digital forensic investigation to appropriately pick out and isolate evidence that is applicable to a particular case or incident. Its miles a measure of ways properly the investigation can distinguish among applicable and irrelevant statistics, and the way correctly it may attribute movements and behaviors to precise individuals. Fig 5:Shows the Computation of Specificity
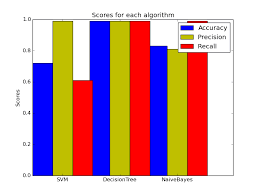
Fig 5: Computation of Specificity
A good way to reap excessive specificity, digital forensic tools and techniques should be capable of appropriately extract and examine statistics from diverse resources along with computer systems, cellular gadgets, and cloud services. This calls for a mixture of technical information, superior tools, and thorough knowledge of investigative strategies. One crucial aspect of specificity is the ability to attribute movements and behaviors to precise individuals. This involves linking digital evidence to a specific person or tool, and being capable of confidently set up who had get right of entry to the device and whilst. This calls for a thorough knowledge of consumer authentication strategies and device usage patterns. Every other key element in accomplishing high specificity is the capacity to filter beside the point records. Digital devices regularly include huge quantities of facts that might not be relevant to a selected research. Therefore, it is crucial to have tools and approaches in region to identify and discard irrelevant statistics, and awareness on the evidence this is maximum applicable to the case. Similarly to technical issues, specificity additionally depends at the investigative strategies utilized by the virtual forensic examiner.
Miss rate
A miss rate, also called a fake terrible fee, is a statistical degree that indicates the share of times a gadget fails to properly understand a particular event or piece of facts. Inside the context of virtual forensics investigations, omit price refers to the failure of a gadget or device to correctly perceive and collect all applicable evidence or data. The miss fee is an important metric in digital forensic investigations due to the fact it may affect the accuracy and completeness of the research. If the leave out charge is excessive, it manner that important proof may be ignored, probably main to inaccurate conclusions or missed possibilities to collect crucial statistics. Several elements can contribute to a high miss rate in virtual forensic investigations. Fig 6:Shows the Computation of Miss rate
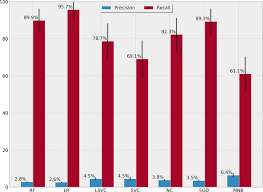
Fig 6: Computation of Miss rate
Those consist of inadequate training or know-how of the investigator, incomplete or previous tools, and the character of the evidence itself (e.g. being hidden or encrypted). It’s also vital to be aware that some degree of omit rate is unavoidable, as virtual forensic investigations often involve complicated and continuously evolving technologies. To lessen the omit rate in digital forensic investigations, it is crucial for investigators to have proper education and knowledge within the modern day digital forensic techniques and tools. They need to additionally stay up to date on advancements in era and be able to adapt their strategies as a consequence.
Conclusion
The belief of tracing human conduct through digital forensic investigations is that digital proof presents an effective device for understanding and analyzing human conduct. Via the evaluation of statistics stored on digital gadgets, investigators can uncover patterns and traits in human conduct, including conversation patterns; net browsing behavior, and monetary transactions. This information can be used to identify suspects, motives, or even are expecting future conduct. Moreover, digital forensic investigations also can aid in fixing crimes and presenting evidence for felony court cases. It’s far obtrusive that virtual forensics plays a critical function in tracing and information human conduct in the digital age.
References
- Mishra, A. K., Hemamalini, V., & Tyagi, A. K. (2024). Digital Forensics with Emerging Technologies: Vision and Research Potential for Future. Conversational Artificial Intelligence, 675-697.
- Dunsin, D., Ghanem, M. C., Ouazzane, K., & Vassilev, V. (2024). A comprehensive analysis of the role of artificial intelligence and machine learning in modern digital forensics and incident response. Forensic Science International: Digital Investigation, 48, 301675.
- Horsman, G. (2024). Sources of error in digital forensics. Forensic Science International: Digital Investigation, 48, 301693.
- Almusayli, A., Zia, T., & Qazi, E. U. H. (2024). Drone Forensics: An Innovative Approach to the Forensic Investigation of Drone Accidents Based on Digital Twin Technology. Technologies, 12(1), 11.
- Odeyemi, O., Ibeh, C. V., Mhlongo, N. Z., Asuzu, O. F., Awonuga, K. F., & Olatoye, F. O. (2024). FORENSIC ACCOUNTING AND FRAUD DETECTION: A REVIEW OF TECHNIQUES IN THE DIGITAL AGE. Finance & Accounting Research Journal, 6(2), 202-214.
- Alam, S., & Altiparmak, Z. (2024). XAI-CF–Examining the Role of Explainable Artificial Intelligence in Cyber Forensics. arXiv preprint arXiv:2402.02452.
- Ansari, N., Dasgupta, J., Umre, S., & Rajput, P. (2024). Harnessing Electron Microscope for Trace Evidence Analysis.
- Babayew, R., Yehuda-Zada, Y., Elgad, N., Lorincik, J., Orion, I., Weiss, A., … & Halevy, I. (2024). Simulation tools for improvement of the fission track analysis method for nuclear forensics. Journal of Radioanalytical and Nuclear Chemistry, 1-17.
- Rani, D., Gill, N. S., & Gulia, P. (2024). A forensic framework to improve digital image evidence administration in IIoT✰. Journal of Industrial Information Integration, 38, 100568.
- El-Kady, R. M. (2024). Investigating Forensic Evidence in Metaverse: A Comparative Analytical Study. In Forecasting Cyber Crimes in the Age of the Metaverse (pp. 227-258). IGI Global.
- Xue, X., Shanmugam, R., Palanisamy, S., Khalaf, O. I., Selvaraj, D., & Abdulsahib, G. M. (2023). A hybrid cross layer with harris-hawk-optimization-based efficient routing for wireless sensor networks. Symmetry, 15(2), 438.
- Suganyadevi, K., Nandhalal, V., Palanisamy, S., & Dhanasekaran, S. (2022, October). Data security and safety services using modified timed efficient stream loss-tolerant authentication in diverse models of VANET. In 2022 International Conference on Edge Computing and Applications (ICECAA) (pp. 417-422). IEEE.
- K. R. K. Yesodha, A. Jagadeesan and J. Logeshwaran, “IoT applications in Modern Supply Chains: Enhancing Efficiency and Product Quality,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 366-371.
- V. A. K. Gorantla, S. K. Sriramulugari, A. H. Mewada and J. Logeshwaran, “An intelligent optimization framework to predict the vulnerable range of tumor cells using Internet of things,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 359-365.
- T. Marimuthu, V. A. Rajan, G. V. Londhe and J. Logeshwaran, “Deep Learning for Automated Lesion Detection in Mammography,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 383-388.
- V. A. Rajan, T. Marimuthu, G. V. Londhe and J. Logeshwaran, “A Comprehensive analysis of Network Coding for Efficient Wireless Network Communication,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 204-210.
- M. A. Mohammed, R. Ramakrishnan, M. A. Mohammed, V. A. Mohammed and J. Logeshwaran, “A Novel Predictive Analysis to Identify the Weather Impacts for Congenital Heart Disease Using Reinforcement Learning,” 2023 International Conference on Network, Multimedia and Information Technology (NMITCON), Bengaluru, India, 2023, pp. 1-8.
- Yadav, S. P., & Yadav, S. (2018). Fusion of Medical Images in Wavelet Domain: A Discrete Mathematical Model. In Ingeniería Solidaria (Vol. 14, Issue 25, pp. 1–11). Universidad Cooperativa de Colombia- UCC. https://doi.org/10.16925/.v14i0.2236
- Yadav, S. P., & Yadav, S. (2019). Mathematical implementation of fusion of medical images in continuous wavelet domain. Journal of Advanced Research in dynamical and control system, 10(10), 45-54.
- Yadav, S.P. (2022). Blockchain Security. In: Baalamurugan, K., Kumar, S.R., Kumar, A., Kumar, V., Padmanaban, S. (eds) Blockchain Security in Cloud Computing. EAI/Springer Innovations in Communication and Computing. Springer, Cham. https://doi.org/10.1007/978-3-030-70501-5_1
