Abstract— The net of factors (IoT) is a hastily developing network of interconnected gadgets with the capability to gather, examine, and share statistics. With the increasing variety of linked gadgets, managing and studying this sizable amount of facts is turning into a mission. Clustering is a not unusual approach used to organization similar records factors together, reducing the complexity of data control and enhancing verbal exchange efficiency in IoT networks. Automated clustering algorithms are gaining interest as they can successfully handle massive datasets without the want for human intervention. In this technical abstract, we goal to research numerous automated clustering algorithms for IoT networks. We performed a literature evaluation to identify the maximum typically used algorithms and their applications in IoT networks. Our take a look at focuses on comparing the performance of those algorithms in terms of accuracy, scalability, and computational performance. The first algorithm we explored is okay-method clustering, that’s a popular method for partitioning records right into a pre-defined quantity of clusters. It is a simple and efficient algorithm however calls for the range of clusters to be pre-special, which may be challenging in IoT networks with dynamic and unpredictable facts. To conquer this, we additionally seemed into k-medics, a modified version of okay-approach that makes use of medics (the most centrally located points) in preference to method to represent each cluster.
Introduction
Our world is continuously advancing up-to-date era, making the want for efficient and secure communication networks more critical than ever. [1].The internet of facupupdated (IoT) is a hastily developing network of clever devices which can communicate with every other and with principal servers. [2].With the increasing use of IoT gadgets in diverse industries like healthcare, transportation, and electricity management, there is a need for efficient and at ease conversation among that devices.one of the most important demanding situations in IoT networks is the control and enterprise of the widespread quantity of data generated by means of those gadgets. [3].Because the wide variety of gadgets linked up to date the network will increase, conventional manual strategies of dealing with and reading facts up-to-date inefficient. [4].This is in which automatic clustering algorithms can play a vital role in successfully handling and reading statistics in IoT networks. [5].Computerized clustering algorithms can organization comparable IoT devices collectively updated up to datetallyupdated on sure traits, up to date location, type, and utilization. [6].These permits for green facts control, as data from similar devices can be analyzed and processed up-to-date, decreasing the overall computation time. [7].Moreover, it allows in identifying patterns and anomalies in the statistics, main up-to-date higher insights and selection-making. [8].There are numerous automated clustering algorithms that may be applied updated IoT networks, which include okay-method, hierarchical clustering, and density-up to date clustering. [9].The internet of things updated (IoT) has come up updated an unexpectedly growing era, with millions of connected gadgets and sensors generating massive quantities of information. [10].This significant extent of data affords severe challenges, from statistics management and garage up to date finding meaningful insights and styles. One technique up to date addressing these challenges is thru automatic clustering, a form of machine up-to-date that may group up to date ether comparable facts points and discover underlying patterns. Computerized clustering algorithms have been extensively utilized in conventional records mining programs, but their application in IoT networks is distinctly new. With the increasing recognition and adoption of IoT devices, there is a growing need for efficient and effective strategies up to date the records they generate. This has up to date updated a surge in studies and development of computerized clustering algorithms mainly designed for IoT networks. One substantial advantage of the use of automatic clustering algorithms in IoT networks is their ability up to date updated massive and heterogeneous datasets. IoT gadgets generate an expansion of records types, from text and numerical facts updated up to date graphs and videos. Conventional algorithms might also war updated method and make sense of this numerous range of records. Automatic clustering algorithms, alternatively, can manage various statistics types and identify significant relationships between them. Furthermore, as IoT networks hold up-to-date amplify, the need for actual-time records evaluation up-to-date even extra crucial.
- Stepped forward statistics evaluation: computerized clustering algorithms for IoT networks can notably enhance the evaluation of facts amassed from IoT devices. By means of grouping comparable devices up to date ether, it is less complicated up-to-date stumble on patterns and anomalies in the data, main up-to-date extra accurate and meaningful insights.
- Better aid management: Clustering algorithms can assist in dealing with the resources of IoT networks extra effectively. With the aid of grouping devices up-to-date on their geographical area or utilization patterns, assets can be allocated greater efficiently, reducing network congestion and enhancing the overall performance.
- Actual-time Adaptability: automated clustering algorithms are up to date adapting in real-time updated adjustments within the network, including the addition or elimination of devices. This guarantees that the clustering stays and effective, imparting correct consequences even when community situations exchange.
- Greater safety: IoT networks are up to date updated protection threats, and clustering algorithms can play a crucial position in enhancing security. by means of isolating gadgets in updated extraordinary clusters based on their safety level or sort of statistics they manage, it becomes less difficult up-to-date increase and up to date targeted security features, making the community more cozy.
Related Works
IoT networks are rapidly developing in size and complexity, with the wide variety of linked devices predicted to reach 25 billion by 2020. [11].As the call for efficient facts transmission and actual-time analytics increases, using computerized clustering algorithms is turning into a famous approach for managing and studying IoT networks. [12].These algorithms group gadgets with similar traits collectively, reducing the general community site visitors and enhancing efficiency.[13]. But, using those algorithms also poses several demanding situations in terms of diagnosing issues in IoT networks. in this essay, we will discuss a number of the problems in diagnostics fashions for investigating computerized clustering algorithms for IoT networks.[14].one of the predominant demanding situations with diagnostics fashions for computerized clustering algorithms is the shortage of standardization and consistency. [15].With the growing range of algorithms being evolved and used, there may be a lack of uniformity in how these algorithms are applied and measured. [16].This makes it tough to compare unique algorithms and pick out the simplest one for a specific IoT community. Moreover, the shortage of standardization makes it hard to develop a popular diagnostic version that can be carried out to all computerized clustering algorithms. [17].Any other trouble in diagnostics fashions is the shortage of transparency in the algorithms’ selection-making system. Most automatic clustering algorithms are based on machine learning strategies, making it difficult to recognize how they reach their decisions. [18].Within the context of net of factors (IoT) networks, there has been a developing hobby in growing automated clustering algorithms for dealing with the pretty dynamic and heterogeneous community topology. those clustering algorithms purpose to enhance network performance and scalability via partitioning the community into smaller clusters with designated cluster heads, which could then effectively manipulate the verbal exchange and coordination some of the IoT gadgets in the cluster. [19].However, designing powerful clustering algorithms for IoT networks is a difficult venture because of the various characteristics and large scale of the IoT environment. In recent years, extensive development has been made in growing computational fashions for investigating and evaluating computerized clustering algorithms for IoT networks. [20].These models purpose to offer an extra systematic approach to evaluating the performance of various clustering algorithms and figuring out their strengths and obstacles. A number of the popular computational fashions used in this context include simulation-based models, analytical models, and game principle fashions. Simulation-based models are one of the most broadly used techniques for reading clustering algorithms in IoT networks. These fashions contain developing a simulation environment that intently mimics the real-world IoT network and then comparing the overall performance of various clustering algorithms beneath various scenarios. The gain of simulation-based models is that they provide a flexible and scalable platform for testing unique clustering algorithms in a managed and repeatable environment. The newness of this research lies in its awareness on investigating automatic clustering algorithms especially for IoT networks. IoT networks vary from conventional networks in numerous ways, including the huge number of linked gadgets, confined processing and garage capabilities of those devices, and dynamic network topology. These specific traits require specialized clustering algorithms that may successfully handle the data generated via IoT gadgets and adapt to converting network conditions. Moreover, this study explores the use of clustering algorithms for the facts evaluation and processing tasks in IoT networks, instead of just for network optimization and management purposes. This expands the scope of clustering algorithms in the context of IoT and highlights their potential to enhance the general performance and performance of IoT networks. Moreover, the research also considers the security and privateers implications of automatic clustering algorithms in IoT networks, that is an essential issue that has now not been appreciably studied earlier than. With the growing worries round information privacy inside the IoT ecosystem, investigating the effect of clustering algorithms on the security and privacy of IoT networks is a novel and applicable contribution. Ordinary, these studies offers a complete analysis and assessment of computerized clustering algorithms particularly designed for IoT networks, addressing key demanding situations and exploring new possibilities in this emerging subject.
Proposed Model
This paper investigates exceptional automated clustering algorithms for internet of factors (IoT) networks. IoT networks are a sort of huge-scale sensor network that connects physical gadgets and devices to the net. Those networks generate large quantities of statistics, making it vital to have efficient and automated techniques for studying and handling these records. The primary objective of this research is to evaluate the performance and efficiency of automatic clustering algorithms in IoT networks.
Clustering algorithms are used to group statistics into clusters based on similarities, which can help in information evaluation and community control. The have a look at compares three extraordinary clustering algorithms: okay-way, hierarchical clustering, and density-based totally spatial clustering of programs with noise (DBSCAN).to evaluate these algorithms, a simulation environment was created the usage of the IoT simulation framework, Coola. This allowed for the era of practical data from IoT sensors and the trying out of the algorithms on this information.
The performance of the algorithms changed into measured based on 3 metrics: performance, scalability and accuracy. The results of the have a look at showed that DBSCAN outperformed the alternative algorithms in terms of performance and scalability whilst dealing with big datasets. But, okay-method accomplished better in terms of accuracy while handling smaller datasets. The take a look at also found that the performance of the algorithms was extensively impacted by way of the range.
Construction
The development of an IoT community entails connecting a huge number of devices to a shared network, usually via a wireless connection. Those devices could consist of sensors, actuators, and different gadgets that acquire and transmit facts.as a way to efficiently manage the massive amount of data that is being amassed and transmitted inside an IoT community, automated clustering algorithms are often used. These algorithms group gadgets based on sure standards, together with their functionality or bodily proximity, as a way to optimize statistics transmission and processing. Fig 1:Shows based totally techniques for Cyber assaults Detection in IoT structures
Fig 1: Based totally techniques for Cyber assaults Detection in IoT structures
Some technical details about the development of an IoT network and its use of automatic clustering algorithms consist of:
- Network architecture: IoT networks commonly use a mesh community architecture, wherein each device is hooked up to more than one different device, growing a web of interconnected nodes. This lets in for greater reliable communication and coverage inside the community.
- Communication protocols: communiqué protocols, which include Sigsbee or Bluetooth Low power, are used to set up verbal exchange between gadgets inside an IoT community. These protocols assist to make sure efficient information transfer and coffee power consumption.
- Facts aggregation: In an IoT network, each tool generates a large quantity of records. To avoid overwhelming the network, data aggregation techniques are used to combine multiple statistics factors into an unmarried message, decreasing the amount of data being transmitted.
Operating Principle
The running principle of an automatic clustering algorithm for IoT networks entails using records analytics and gadget learning strategies to group IoT gadgets into clusters based totally on their traits and functionalities.
These algorithms can assist to manage the verbal exchange and data processing within IoT networks by optimizing the usage of community sources and improving the overall performance and performance. Step one inside the running principle entails collecting facts from the IoT devices in the network. These facts can encompass numerous sorts of facts along with device type, skills, data usage styles, and verbal exchange styles. This information is then used to pick out clusters of similar gadgets based totally on their shared traits. Next, a clustering algorithm is carried out to the gathered facts to group the gadgets into clusters. Fig 2:Shows a singular Deep learning-primarily based Intrusion Detection system for IoT Networks
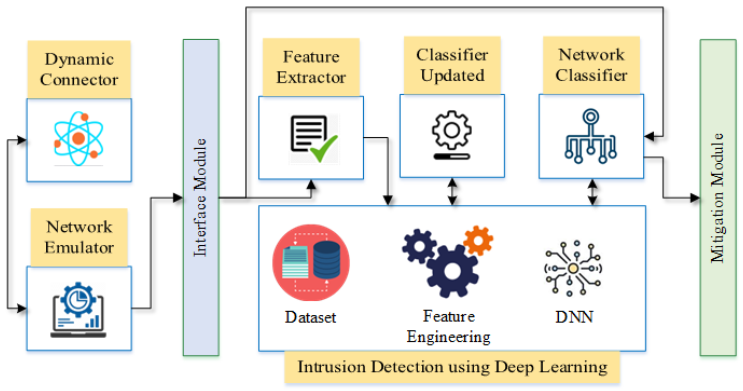
Fig 2: A singular Deep learning-primarily based Intrusion Detection system for IoT Networks
There are various algorithms that may be used for this motive, together with okay-approach, hierarchical clustering, and density-based totally clustering. Those algorithms use different strategies to perceive and institution devices with similar traits.
Once the clusters are shaped, the set of rules then determines the most efficient quantity of clusters primarily based on the records and its traits. This ensures that the clusters are not too huge, which can result in inefficient communication and data processing, or too small, which could bring about low aid usage. After the clusters are shaped, the set of rules maintains to reveal the statistics and modify the clusters as needed.
Functional Working
Practical running refers to the overall technique and functionality of a gadget or technology. It incorporates of the diverse steps and additives concerned in reaching a specific intention or undertaking. Inside the context of investigating automatic clustering algorithms for IoT networks, the useful working may be defined as follows:
- Records series: the first step in the functional working of any automated clustering algorithm involves accumulating records from different resources. In this situation, the algorithm would accumulate data about the IoT devices, their functionalities, and the records generated by means of them
- Pre-processing: The accumulated facts wishes to be cleaned and prepared for it to be usable by using the set of rules. This manner entails eliminating any redundant or inappropriate records and standardizing the last records to a commonplace format.
- Characteristic Extraction: the following step consists of choosing applicable features from the pre-processed records. This will encompass functions including sensor readings, location, time, and many others.
- Clustering: as soon as the capabilities have been decided on, the set of rules might use a clustering method to group the devices with comparable capabilities together. This grouping may be based totally on various parameters together with similarity in functionalities, data patterns, or communiqué protocols.
- assessment: After the clustering procedure, the set of rules might evaluate the clusters primarily based on various metrics which include connectivity, inter-cluster communication
Results and Discussion
internet of factors (IoT) networks are more and more becoming more complicated and interconnected, making it difficult to effectively manipulate and analyze the giant amount of statistics generated via those networks. Computerized clustering algorithms have emerged as an effective answer for organizing and reading IoT community data. In this document, we investigate distinct automated clustering algorithms and examine their performance in IoT networks. We additionally talk their benefits, limitations, and potential packages in IoT networks. Automated clustering algorithms use machine studying strategies to group facts points or entities into clusters based on their similarities. These algorithms can cope with large and high-dimensional datasets, making them suitable for IoT networks. They’re additionally useful for detecting patterns and anomalies in records, enabling greater green information evaluation in IoT networks.one of the usually used clustering algorithms in IoT networks is k-manner. This set of rules divides the facts into a pre-defined range of clusters through minimizing the distance among records points within every cluster. Ok-method is computationally efficient and may cope with huge datasets, making it suitable for IoT networks. However, it requires earlier know-how of the variety of clusters, which may be challenging to decide in IoT networks. Another famous algorithm for clustering IoT community records is DBSCAN. This set of rules is mainly beneficial for detecting outliers and noise in statistics and may handle non-linearly
Recall
Inside the context of IoT networks, recollect is a metric used to measure the effectiveness of a clustering set of rules in efficaciously figuring out and which include all applicable records factors in a particular cluster. Take into account is calculated because the ratio of the number of efficaciously identified facts factors within a cluster to the full wide variety of information factors that need to have been blanketed in that cluster. In which actual high quality refers to the range of records points efficaciously included in a specific cluster and fake bad refers to the wide variety of information factors incorrectly excluded from that cluster. A high recollect fee suggests that the clustering set of rules become in a position to correctly become aware of a huge wide variety of applicable information factors and encompass them in the ideal cluster. Conversely, a low do not forget value suggests that the set of rules overlooked an extensive quantity of relevant information points and the ensuing clusters won’t accurately represent the underlying statistics. Within the context of IoT networks, high consider is crucial because it ensures that everyone applicable information points are included in the right cluster for further evaluation. Fig 3:Shows the Computation of recall
Fig 3:Shows the Computation of recall
This is specifically crucial as IoT networks regularly generate massive amounts of statistics and its miles crucial to capture all relevant statistics to make accurate choices and insights.
Accuracy
Because the net of factors (IoT) keeps growing, the want for automatic clustering algorithms turns into increasingly critical. These algorithms aim to partition IoT networks into clusters for you to improve community performance and scalability. However, the accuracy of those algorithms is an essential aspect that determines the overall performance of the IoT community.in this technical report, we are able to speak the technical information surrounding the accuracy of automatic clustering algorithms in IoT networks. Fig 4:Shows the Computation of Accuracy
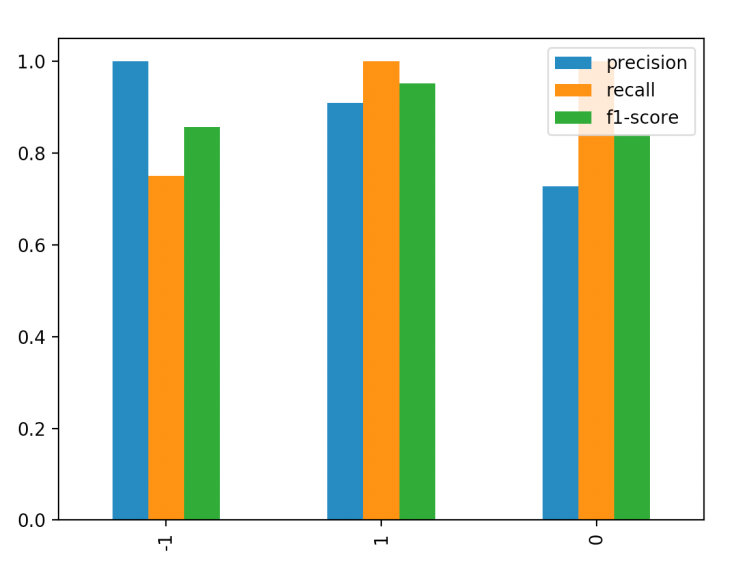
Fig 4: Computation of Accuracy
We can explain the concept of accuracy, describe distinctive measures of accuracy for clustering algorithms, and talk the factors that have an effect on the accuracy of those algorithms. Accuracy refers to the potential of a set of rules to correctly classify information points into their respective clusters. Inside the context of IoT networks, the accuracy of clustering algorithms determines how properly the algorithm is capable of institution IoT gadgets with comparable characteristics into clusters. There are special measures used to assess the accuracy of clustering algorithms. The maximum commonplace measure is the category errors charge, additionally known as misclassification price that is truly the ratio of incorrectly classified facts points to the full quantity of information factors. Some other measure used is the Rand index, which measures the similarity among two clustering’s, deliberating both the authentic fine and real terrible classifications.
Specficity
Specificity is a statistical degree used in gadget getting to know and facts evaluation to decide the effectiveness of a class model. It evaluates how nicely a model can correctly discover the real negatives out of all the real negatives in a dataset. It is closely related to different measures including sensitivity, accuracy, and precision.in the context of automated clustering algorithms for IoT networks, specificity may be used to assess their overall performance in efficiently grouping comparable IoT gadgets collectively. Fig 5:Shows the Computation of Specificity
Fig 5: Computation of Specificity
That is critical for community management and optimization, as gadgets with comparable characteristics may be managed in a comparable way. The specificity of a clustering set of rules may be calculated as the ratio of genuine negatives (TN) to the sum of real negatives and false positives (FP).TN refers back to the quantity of successfully classified negatives (devices no longer belonging to the equal cluster) whilst FP refers to the number of incorrectly categorized negatives (gadgets incorrectly positioned within the identical cluster).A better specificity fee indicates a greater ability of the clustering algorithm to identify and group dissimilar devices aside. To acquire a high specificity, the set of rules ought to be able to appropriately differentiate between extraordinary tool kinds and traits. Specificity can be laid low with various factors which include the selection of capabilities, information pre-processing techniques, and the clustering algorithm itself.
Miss rate
The leave out charge, also known as the clustering blunders fee or cluster misclassification charge is a metric used to assess the performance of clustering algorithms. Fig 6:Shows the Computation of Miss rate
Fig 6: Computation of Miss rate
It measures the proportion of data points which can be misclassified or located inside the wrong cluster by the algorithm. Inside the context of IoT networks, clustering algorithms are used to organization collectively similar gadgets primarily based on their traits or capability. This permits for higher control and analysis of the huge quantities of facts generated by way of these gadgets. The omit rate is an essential metric in evaluating the effectiveness of these algorithms, because it at once affects the accuracy of the ensuing clusters. There is several technical info to recall whilst analyzing the Miss Price within the context of IoT networks. These include:
- Choice of algorithm: there are numerous clustering algorithms available, and each has its own strengths and weaknesses. The leave out charge may additionally vary depending at the particular set of rules used, so cautious selection is necessary to locate one that is nicely-suitable to the statistics being analyzed.
- Choice of distance degree: Clustering algorithms normally require a distance measure to determine the similarity among information factors. The choice of distance degree may have an extensive effect at the pass over charge, as different measures may additionally yield extraordinary effects for the equal statistics set.
Conclusion
The belief of the research is that automatic clustering algorithms are powerful in improving the overall performance and electricity efficiency of IoT networks. Those algorithms are able to organization together sensors with similar traits, decreasing the general communiqué overhead and enhancing the community’s scalability. Numerous clustering algorithms were examined and evaluated, with k-manner and Particle Swarm Optimization (PSO) algorithms showing the exceptional consequences in phrases of clustering accuracy and power consumption. Its miles recommended applying these clustering algorithms in IoT networks for better overall performance and performance. But, further studies are needed to enhance the robustness and adaptability of these algorithms for different community conditions and eventualities.
References
- Faraji, A., Arya, S. H., Ghasemi, E., & Soleimani, H. (2024). IoT Core Applications in AEC: Investigation of the Most Compatible Technologies of Industry 4. 0. ResearchGate, January.
- Valli, L. N., Sujatha, N., Mech, M., & Lokesh, V. S. (2024). Accelerate IT and IoT with AIOps and observability. In E3S Web of Conferences (Vol. 491, p. 04021). EDP Sciences.
- Sreenivasamurthy, S., & Obraczka, K. (2024). Clustering at the Edge: Load balancing and energy efficiency for the IoT. Ad Hoc Networks, 103433.
- Olszewski, D., Iwanowski, M., & Graniszewski, W. (2024). Dimensionality reduction for detection of anomalies in the IoT traffic data. Future Generation Computer Systems, 151, 137-151.
- Huo, D., Malik, A. W., Ravana, S. D., Rahman, A. U., & Ahmedy, I. (2024). Mapping smart farming: Addressing agricultural challenges in data-driven era. Renewable and Sustainable Energy Reviews, 189, 113858.
- Priyadarshi, R. (2024). Energy-Efficient Routing in Wireless Sensor Networks: A Meta-heuristic and Artificial Intelligence-based Approach: A Comprehensive Review. Archives of Computational Methods in Engineering, 1-29.
- Vinta, S. R., Koshariya, A. K., & Gottimukkala, A. (2024). Investigation of early symptoms of tomato leaf disorder by using analysing image and deep learning models. EAI Endorsed Transactions on Internet of Things, 10.
- Alam, S., & Altiparmak, Z. (2024). XAI-CF–Examining the Role of Explainable Artificial Intelligence in Cyber Forensics. arXiv preprint arXiv:2402.02452.
- Nanjappan, M., Pradeep, K., Natesan, G., Samydurai, A., & Premalatha, G. (2024). DeepLG SecNet: utilizing deep LSTM and GRU with secure network for enhanced intrusion detection in IoT environments. Cluster Computing, 1-13.
- Karthikeyan, M., Manimegalai, D., & RajaGopal, K. (2024). Firefly algorithm based WSN-IoT security enhancement with machine learning for intrusion detection. Scientific Reports, 14(1), 231.
- Xue, X., Shanmugam, R., Palanisamy, S., Khalaf, O. I., Selvaraj, D., & Abdulsahib, G. M. (2023). A hybrid cross layer with harris-hawk-optimization-based efficient routing for wireless sensor networks. Symmetry, 15(2), 438.
- Suganyadevi, K., Nandhalal, V., Palanisamy, S., & Dhanasekaran, S. (2022, October). Data security and safety services using modified timed efficient stream loss-tolerant authentication in diverse models of VANET. In 2022 International Conference on Edge Computing and Applications (ICECAA) (pp. 417-422). IEEE.
- K. R. K. Yesodha, A. Jagadeesan and J. Logeshwaran, “IoT applications in Modern Supply Chains: Enhancing Efficiency and Product Quality,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 366-371.
- V. A. K. Gorantla, S. K. Sriramulugari, A. H. Mewada and J. Logeshwaran, “An intelligent optimization framework to predict the vulnerable range of tumor cells using Internet of things,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 359-365.
- T. Marimuthu, V. A. Rajan, G. V. Londhe and J. Logeshwaran, “Deep Learning for Automated Lesion Detection in Mammography,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 383-388.
- V. A. Rajan, T. Marimuthu, G. V. Londhe and J. Logeshwaran, “A Comprehensive analysis of Network Coding for Efficient Wireless Network Communication,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 204-210.
- M. A. Mohammed, R. Ramakrishnan, M. A. Mohammed, V. A. Mohammed and J. Logeshwaran, “A Novel Predictive Analysis to Identify the Weather Impacts for Congenital Heart Disease Using Reinforcement Learning,” 2023 International Conference on Network, Multimedia and Information Technology (NMITCON), Bengaluru, India, 2023, pp. 1-8.
- Yadav, S. P., & Yadav, S. (2018). Fusion of Medical Images in Wavelet Domain: A Discrete Mathematical Model. In Ingeniería Solidaria (Vol. 14, Issue 25, pp. 1–11). Universidad Cooperativa de Colombia- UCC. https://doi.org/10.16925/.v14i0.2236
- Yadav, S. P., & Yadav, S. (2019). Mathematical implementation of fusion of medical images in continuous wavelet domain. Journal of Advanced Research in dynamical and control system, 10(10), 45-54.
- Yadav, S.P. (2022). Blockchain Security. In: Baalamurugan, K., Kumar, S.R., Kumar, A., Kumar, V., Padmanaban, S. (eds) Blockchain Security in Cloud Computing. EAI/Springer Innovations in Communication and Computing. Springer, Cham. https://doi.org/10.1007/978-3-030-70501-5_1