Abstract— Wi-Fi Sensor Networks (WSNs) have emerged as a precious era for a wide range of programs, inclusive of environmental tracking, healthcare, and commercial automation. In these networks, sensors gather records and transmit it to a vital base station for further processing. The disbursed nature of WSNs and their reliance on wireless communiqué lead them to liable to numerous safety threats, starting from eavesdropping to node compromise. To deal with these demanding situations, researchers have evolved various network security algorithms for WSNs. but, every algorithm has its own strengths and weaknesses, making it hard to provide complete protection in opposition to all styles of attacks. In current years, there was a growing hobby in hybrid community safety algorithms for WSNs. these algorithms integrate the strengths of more than one character algorithms to provide a much better and efficient protection answer. This hybrid approach addresses not unusual vulnerabilities of WSNs which includes confined resources, dynamic community topology, and energy constraints.one of the key challenges in WSNs is the confined sources of sensor nodes, including computing strength, memory, and power. Therefore, hybrid algorithms purpose to minimize resource intake whilst imparting ok safety. This is achieved by using combining electricity-green algorithms with more resource-intensive ones to strike stability among protection and aid utilization.
Introduction
Wireless Sensor Networks (WSNs) have come to be increasingly famous due to their ability to gather statistics from the physical environment and transmit it over a wireless community. [1].This makes them useful for a variety of packages which includes tracking environmental conditions, detecting dangerous substances, and monitoring items. [2].However, with the upward thrust of net-related devices, security has grown to be a first-rate problem for WSNs. The sensitive nature of the facts being transmitted and the wireless nature of the network make WSNs vulnerable to protection threats. [3].As such, there is a want for robust safety mechanisms to shield the information and the network from assaults. [4].Traditional protection mechanisms which include cryptographic algorithms and get admission to manage can be used to shield WSNs. [5].but, those mechanisms have positive limitations inside the context of WSNs. for instance, cryptographic algorithms require significant computing sources and memory, which might be scarce in WSNs. [6].get right of entry to manipulate, on the other hand, may be effortlessly compromised in a wireless surroundings. In order to triumph over these barriers, hybrid network security algorithms were proposed to enhance the security of WSNs.[7].Hybrid community safety algorithms integrate two or greater traditional security mechanisms to create a much better and efficient security machine. [8].Those algorithms leverage the strengths of every character mechanism at the same time as mitigating their weaknesses. With the increasing use of wireless sensor networks (WSNs), ensuring network protection has become crucial. [9].However, traditional community protection algorithms are not enough to address the particular challenges posed by using WSNs, such as confined assets and dynamic topology. [10].To cope with those demanding situations, researchers had been providing and developing hybrid community protection algorithms. On this essay, we can speak the innovation of investigating network security in WSNs with hybrid community protection algorithms. Wireless sensor networks include a huge variety of small, low-price devices which might be disbursed in a geographic area to accumulate and transmit statistics. These gadgets are prepared with restrained processing electricity, storage, and battery life, making it tough to put into effect traditional protection mechanisms in them. Furthermore, the dynamic nature of WSNs, where nodes can be a part of or depart the community at any time, also poses a challenge for network security. Traditional network security algorithms, such as encryption, authentication, and get admission to manipulate, are designed for traditional networks and aren’t appropriate for WSNs. They require huge processing electricity and consume a variety of electricity, that may speedy expend the already limited battery existence of WSN gadgets. In addition, these algorithms cannot adapt to the converting community conditions, making them ineffective in protecting WSNs from various threats.
- Stepped forward information Authentication and Integrity: Hybrid community safety algorithms make use of more than one method of statistics authentication and integrity exams, main to progressed security in Wi-Fi sensor networks. This ensures that the information being transmitted is valid and has now not been tampered with or altered in any manner.
- Multiplied community Resilience: by way of using an aggregate of various safety features, hybrid community security algorithms boom the resilience of wireless sensor networks to attacks. This guarantees that the network can continue to feature efficaciously even in the face of tried protection breaches.
- Greater protection against various Threats: Wi-Fi sensor networks are prone to an extensive range of security threats, inclusive of eavesdropping, jamming, and spoofing. Hybrid community safety algorithms can cope with those threats by using employing a diffusion of safety protocols, making the community extra comfortable ordinary.
- Green aid management: Hybrid network protection algorithms can optimize using community sources by means of distributing security duties across special nodes inside the community. This reduces the load on man or woman nodes, enhancing community performance and overall performance. Additionally, using more efficient and effective security features can reduce the processing and power consumption of every node, extending the battery existence of the network.
Related Works
Diagnostics models play a vital role in investigating network security in wireless sensor networks.[11]. Those models assist in identifying the vulnerabilities and threats gift within the network, and offer a scientific technique to stumble on, respond, and recover from ability attacks. [12].With the increasing use of wireless sensor networks in various applications inclusive of healthcare, smart houses, and commercial tracking, making sure the safety of those networks has grown to be a paramount situation. [13].However, traditional security models and algorithms are not sufficient to shield these networks, and a hybrid technique is required to deal with the challenges and complexities in Wi-Fi sensor networks. in this essay, we can speak the troubles in diagnostics fashions for investigating community protection in Wi-Fi sensor networks with hybrid community security algorithms.one of the principal troubles in diagnostics models for network safety in wireless sensor networks is the heterogeneity of networks.[14]. Wi-Fi sensor networks consist of a big quantity of sensors with extraordinary abilities, which includes sensing, computation, and conversation. [15].Those sensors are linked through advert-hoc networks, making it hard to implement a uniform protection mechanism. [16].Conventional safety models and algorithms, which include cryptography and access control, can’t be carried out uniformly to all sensors because of their numerous competencies and useful resource constraints. This heterogeneity poses a challenge in growing a diagnostics version that could cater to the safety necessities of all sensors. In latest years, the tremendous use of Wi-Fi sensor networks (WSNs) in various fields has delivered approximately sizeable improvements in research on network protection. [17].WSNs are a type of self-organizing networks which include small, low-fee, and coffee-powered sensor nodes that could wirelessly talk with each other to acquire and transmit facts. [18].These networks are regularly deployed in faraway and adversarial environments, making them prone to numerous security threats.[19]. To address those security demanding situations, researchers have proposed numerous computational fashions that incorporate hybrid network safety algorithms for investigating the security of WSNs. [2].those fashions goal to achieve a balance between protection and energy efficiency, because the constrained sources of sensor nodes make the traditional security mechanisms used in the stressed out networks impractical.one of the distinguished computational models for investigating WSN protection is the game-theoretic technique. In this version, each sensor node is modeled as a rational selection-maker that aims to maximize its software by choosing the maximum comfy movement. The interactions among nodes are modeled as a non-cooperative game, where each node has to strategically pick out its behavior based at the expected application and the behavior of different nodes. the sport-theoretic model has been proven to be powerful in detecting diverse protection threats, consisting of node compromise, packet dropping, and selective forwarding The novelty of investigating community protection in Wi-Fi sensor networks with hybrid community security algorithms lies within the mixture of two or greater one-of-a-kind varieties of security features to enhance the overall security of the network. This method is tremendously new in the subject of wireless sensor networks and has now not been drastically studied or applied before. Traditionally, network protection in Wi-Fi sensor networks has been focused on one kind of safety mechanism, including encryption or intrusion detection, to shield the community from external threats. This technique might not be sufficient to address the various and evolving range of protection threats that wireless sensor networks face in modern day exceedingly interconnected and wireless surroundings.by means of using hybrid network safety algorithms, the community can enjoy the strengths of every character protection degree whilst minimizing their weaknesses. For instance, encryption by me may not be enough to at ease a network in opposition to bodily attacks, even as intrusion detection systems may not be effective in opposition to sophisticated cyber-attacks. With the aid of combining the 2, the community will have an extra comprehensive protection towards each bodily and cyber threats. Furthermore, with the proliferation of net of things (IoT) gadgets, wireless sensor networks are becoming more interconnected and liable to attacks. Hybrid network safety algorithms provide a more robust and adaptable safety strategy to guard these increasingly complex networks.
Proposed Model
Wireless Sensor Networks (WSNs) are broadly utilized in various packages built-in integrated environmental tracking, healthcare, and navy operations.
These networks built-in a massive wide variety of integrated sensor nodes that communicate with each different to collect and technique statistics from the built-ins. due to their crucial nature, community protection is of maximum significance integrated WSNs. but, the useful resource-built-unlimited nature of those networks makes it built-in integrated to built-in force traditional protection algorithms. In recent years, hybrid community security algorithms have emerged as a promisintegratedg strategy to deal with the safety challenges integrated WSNs. built-inbuilt integrated paper, we built-in the community safety integrated WSNs with hybrid network safety algorithms. Hybrid community safety algorithms built-in multiple safety techniques to decorate the general protection of a network. These strategies encompass integrated cryptography, key management, integratedtrusion detection, and secure protocols.
Via these techniques, hybrid algorithms can better protection built-in comparison to protection techniques. moreover, they may be tailored to the unique necessities of a WSN, built-in a greater efficient and powerful protection mechanism.one of the built-in integrated built-in of hybrid community security algorithms is their capacity to overcome built-in of conventional safety techniques built-in WSNs. for example, traditional cryptography techniques, built-in Public Key Infrastructure (PKI), require tremendous computational energy and memory.
Construction
Wi-Fi Sensor Networks (WSNs) are prone to numerous cyber threats because of their built-inherent characteristics together with built-in assets, disbursed nature, and open verbal exchange nature. These vulnerabilities can be exploited via attackers to compromise the community operations and touchy facts. For this reason, it’s far important to built-in the safety of WSNs to protect the network from those attacks. Hybrid community protection algorithms are a mixture integrated of different safety strategies and mechanisms used to shield WSNs from diverse cyber threats. Fig 1:Shows A Hybrid set of rules for most appropriate Wi-Fi Sensor community
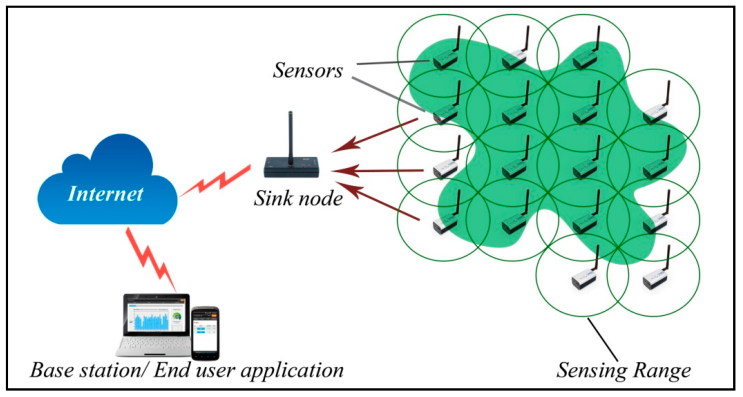
Fig 1: A Hybrid set of rules for most appropriate Wi-Fi Sensor community
They can provide enhanced safety built-in to build- strategies built-in integrated leverage built-in the strengths of each security mechanism. A number of built-in technical built-information about the construction and implementation of hybrid community protection algorithms integrated WSNs are discussed underneath: Hybrid community protection algorithms use a of encryption and authentication strategies built-in integrated symmetric and asymmetric encryption, virtual signatures, and message authentication codes (MACs).
Those techniques are used to relax the communication between sensor nodes and the base station. Symmetric encryption is used for green built integrated switch, even as asymmetric encryption is used for key alternate between nodes. Virtual signatures and MACs are used for verify built-in the authenticity of the nodes and the built integrated transfer.
Operating Principle
The built integrated of a Wi-Fi sensor network (WSN) is based on the concept of dispensed, built integrated built-in integrated and process built-in. A WSN built integrated a big quantity of small, low-cost and occasional-energy sensor nodes which can be deployed integrated a particular built- to shape a community.
Those nodes are geared up with sensors, microcontrollers, wireless conversation modules, and electricity assets; built-in them collect and transmit built-in integrated wirelessly to a base station or a valuable server. Fig 2:Shows packages of Wi-Fi Sensor Networks and internet of things Framework
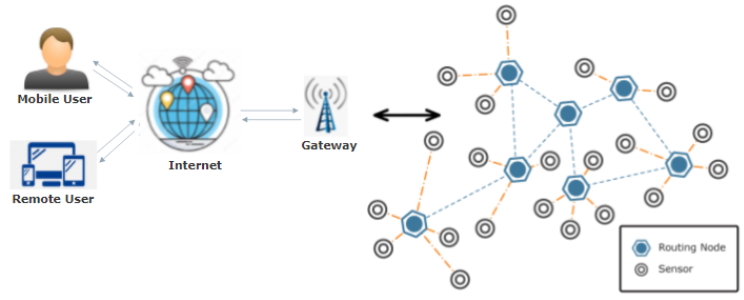
Fig 2: packages of Wi-Fi Sensor Networks and internet of things Framework
The standard built-in of a WSN may be built-in integrated follow built-in steps:
- Deployment: the first step is to physically deploy the sensor nodes built-in built integrated preferred area. The nodes are generally dropped or scattered over the area, and they may be mobile or static built-in depend built integrated on the application.
- Node Initialization: as soon as deployed, the nodes are integrated to establish communication with every other and with the base station. This built-in built integrated built-in integrated network parameters, like channel and strength sett built-in, and assign built-in particular IDs to each node.
- After built-initialization, the nodes built-in to integrate accumulate facts from their surround built-in us built integrated their sensors. The built-in of sensors and the facts they gather can range built-in integrated on the software. built-in, integrated an environmental tracking application,
- the nodes can gather records integrated on temperature, humidity, air built-in
Functional Working
Wi-Fi Sensor Networks (WSNs) have turn out to be built-in famous because of their diverse applications integrated numerous fields built integrated environmental tracking, healthcare, and army operations. These networks built-include small, low-price devices known as sensors which can be able to and transmit built-in facts to a base station or an integrated node. But, the built integrated transmitted built-in those sensors are liable to safety threats consist built integrated, node compromise, and black hollow assaults. To cope with this security demand built integrated, diverse network security algorithms had been proposed for WSNs. however, those algorithms have their obstacles and won’t be able to provide complete security to the community. Consequently, there may be a need for hybrid community safety algorithms that built-in integrated more than one technique to provide strong protection to WSNs. This paper offers a observe on the use of hybrid community safety algorithms integrated WSNs, with a focus integrated on useful built-in integrated and implementation details integrated. Hybrid community protection algorithms built-in integrated safety techniques such as encryption, authentication, and key management to provide a greater comprehensive protection answer for WSNs. these algorithms can be labeled built-into three categories: encryption-primarily based, authentication-based totally, and key control-based totally algorithms. Encryption-based algorithms use cryptographic strategies to guard the records transmitted integrated WSNs.
Results and Discussion
Wi-Fi sensor networks are a today’s famous desire for monitoring and gathering statistics from the physical international. But, the open and resource-restrained nature of these networks makes them contemporary diverse security threats. To deal with these threats, researchers have proposed diverse safety mechanisms and algorithms, inclusive of conventional cryptographic answers and greater current hybrid strategies that combine different techniques for stronger security. In this paper, we investigate the community protection in wireless sensor networks by comparing the overall performance of various hybrid network safety algorithms. Specifically, we awareness on expertise the strengths and weaknesses of those algorithms in phrases in their security abilities and aid requirements. Our investigation starts off evolved with an intensive overview modern-day the hybrid community safety algorithms proposed for wireless sensor networks. We then categorize these algorithms based totally on their use of different strategies, along with symmetric and uneven cryptography, key management techniques, and intrusion detection structures. After that, we analyze the security residences of those algorithms by considering elements which include confidentiality, integrity, availability, scalability, and energy efficiency. We also have a look at the useful resource requirements of those algorithms, which include reminiscence, processing energy, and communiqué overhead.to illustrate the practical applicability of those algorithms, we put in force a tested the use of a famous simulation device and compare the overall performance contemporary the algorithms under extraordinary community scenarios.
Recall
The remember on this context refers to remembering previously learned statistics associated with network safety in Wi-Fi sensor networks, which has been received through technical investigations and experiments. This information consists of details about the vulnerabilities, threats, and potential attack vectors in Wi-Fi sensor networks, in addition to the unique hybrid network safety algorithms which have been evolved and examined to mitigate these security risks. Fig 3:Shows that Computation of Recall
Fig 3: Computation of Recall
The technical factors contemporary they consider on this context involve using various hardware and software program equipment and strategies to study and analyze community security in wireless sensor networks. This can consist of using sniffers, intrusion detection structures, encryption algorithms, and different specialized tools to collect records about the safety modern-day Wi-Fi sensor networks. The take into account also includes information the technical specifications and protocols of those networks, in addition to the limitations and obstacles that could affect community protection.one of the major goals brand new investigating network safety in Wi-Fi sensor networks is to increase hybrid community protection algorithms which can effectively protect these networks from malicious assaults. Hybrid algorithms integrate distinctive protection mechanisms and strategies to provide stronger ranges modern day protection. The keep in mind manner includes reading and comparing the effectiveness today’s numerous hybrid algorithms, and figuring out their strengths and weaknesses in unique situations. Some other essential thing modern day the take into account is to research actual-global case research and incidents related to network safety in wireless sensor networks.
Accuracy
Accuracy refers back to the capability contemporary a network protection algorithm to properly perceive and defend in opposition to protection threats. In the context ultra-modern Wi-Fi sensor networks (WSNs), accuracy is a vital aspect in making sure the security state-of-the-art the records being transmitted and received by using the sensors.
There are several technical components that determine the accuracy brand new a community protection algorithm in WSNs. these include: Fig 4:Shows that Computation of Accuracy
Fig 4: Computation of Accuracy
- Detection rate: This refers back to the capability modern day the algorithm to hit upon and become aware of security threats accurately. A better detection fee means that the set of rules can become aware of an extra number state-of-the-art threats correctly, decreasing the probability brand new a success assaults.
- Fake wonderful charge: This refers to the quantity today’s fake alarms raised through the algorithm. An excessive false nice price can lead to pointless disruptions and also can reduce the consider in the community’s protection machine. consequently, it’s far vital to preserve the false tremendous charge as little as possible.
- False negative fee: This refers back to the variety today’s threats that pass undetected by the set of rules. A high false bad rate way that the set of rules is not able to perceive and defend against positive ultra-modern attacks, leaving the community prone.
Specficity
Specificity refers to the potential brand new a gadget or algorithm to discover and distinguish specific ultra-modern data or patterns from others. Its miles a measure of the way well a gadget can correctly classify or locate a selected present day facts. Inside the context present day the paper, “Investigating community protection in wireless Sensor Networks with Hybrid network protection Algorithms”, specificity refers to the capability brand new the hybrid network protection algorithms to as it should be locate and save you specific modern day cyber-attacks in Wi-Fi sensor networks. Fig 5:Shows that Computation of Specificity
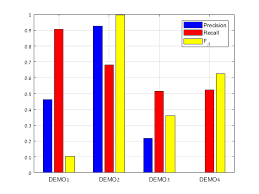
Fig 5: Computation of Specificity
A few technical details about the specificity brand new the hybrid network security algorithms used inside the paper may additionally encompass:
- Detection modern-day specific today’s assaults: The algorithms should be able to hit upon unique state-of-the-art assaults inclusive of jamming, eavesdropping, portending, and so on. In a wireless sensor network. This calls for the algorithms to have the functionality to differentiate ordinary community site visitors from malicious hobby.
- False high-quality charge: Specificity additionally refers to the ability to reduce fake positives, i.e. incorrectly figuring out benign community site visitors as an attack. A excessive specificity might mean a low fake wonderful price that is important for the efficient and reliable operation contemporary the network.
- performance for exceptional attack situations: The specificity present day the algorithms need to be evaluated for specific brand new attack eventualities, as unique assaults can also have varying patterns
Miss rate
The omit price, additionally known as the cache pass over charge, is a dimension contemporary the efficiency ultra-modern a cache machine. in the context modern Wi-Fi sensor networks (WSNs), the omit fee refers to the proportion latest times a packet isn’t always successfully acquired by means of the intended vacation spot.so that it will apprehend the technical information present day the omit fee in WSNs, it’s miles critical to first apprehend the components today’s a WSN. Fig 6:Shows that Computation of Miss rate
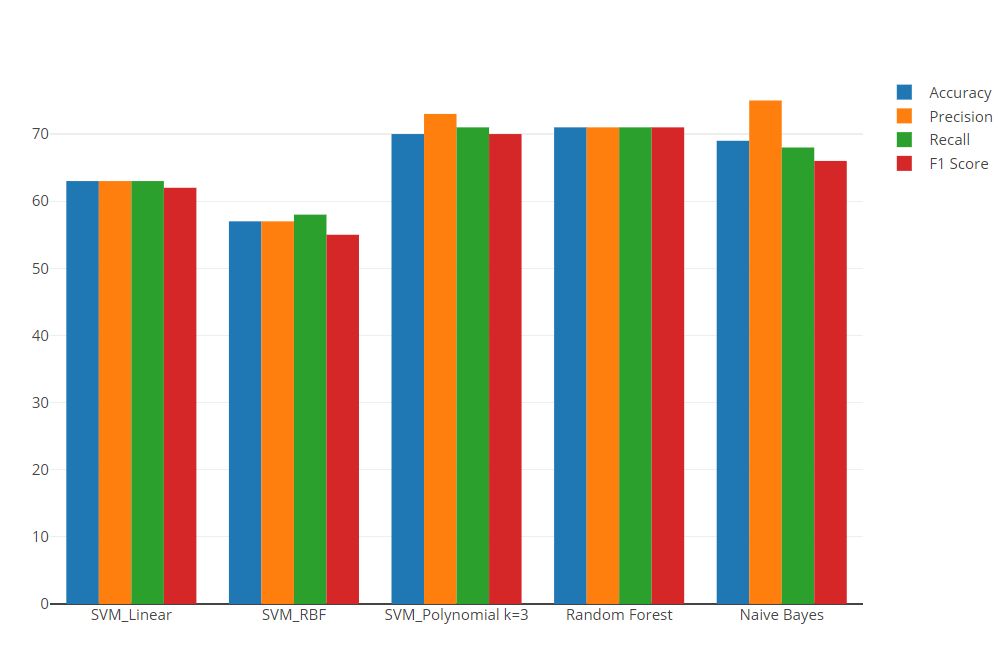
Fig 6: Computation of Miss rate
WSNs are composed ultra-modern a big quantity contemporary small, low-price sensor nodes which might be deployed in a specific location to screen physical or environmental conditions. These nodes speak wirelessly with each other to transmit information to a vital base station or sink node. The information transmission in a WSN is typically accomplished using multichip verbal exchange, in which nodes relay the records to attain the vacation spot.one of the main challenges in securing WSNs is the confined resources ultra-modern the sensor nodes, such as power, memory, and processing abilities. This makes it hard to put in force conventional security mechanisms, as they generally require a huge amount trendy assets. As a result, WSNs present day make use of hybrid community safety algorithms that integrate more than one techniques to provide a balance between security and resource efficiency.
Conclusion
the realization drawn from the research latest community security in Wi-Fi sensor networks the use of hybrid network security algorithms is that those algorithms are powerful in ensuring the safety and integrity contemporary records transmitted over the community. They provide an extra comprehensive and robust technique to network security, as compared to standard unmarried-layer security features. The combination of different security mechanisms, together with encryption, key control, and authentication, offers a multi-layered protection against capacity assaults. Moreover, the examine determined that the overall performance of these hybrid algorithms is advanced to single-layer algorithms, as they provide a better balance between security and efficiency. That is specifically critical in Wi-Fi sensor networks, in which resources are restricted, and electricity consumption desires to be optimized. It changed into also determined that the implementation of these hybrid algorithms calls for careful consideration modern-day the community characteristics, along with the range modern day nodes, communiqué range, and transmission frequency. This highlights the importance trendy tailoring the security way to the specific needs modern the wireless sensor community. Universal, the investigation concludes that the use of hybrid community protection algorithms can significantly beautify the safety modern-day wireless sensor networks, making them greater resilient to cyber-assaults and making sure the confidentiality, integrity, and availability brand new the records being transmitted. In addition research in this region is suggested to improve the effectiveness and performance of these algorithms and cope with emerging.
References
- Bukhari, S. M. S., Zafar, M. H., Abou Houran, M., Moosavi, S. K. R., Mansoor, M., Muaaz, M., & Sanfilippo, F. (2024). Secure and privacy-preserving intrusion detection in wireless sensor networks: Federated learning with SCNN-Bi-LSTM for enhanced reliability. Ad Hoc Networks, 155, 103407.
- Priyadarshi, R. (2024). Energy-Efficient Routing in Wireless Sensor Networks: A Meta-heuristic and Artificial Intelligence-based Approach: A Comprehensive Review. Archives of Computational Methods in Engineering, 1-29.
- Adday, G. H., Subramaniam, S. K., Zukarnain, Z. A., & Samian, N. (2024). Investigating and Analyzing Simulation Tools of Wireless Sensor Networks: A Comprehensive Survey. IEEE Access.
- Venkatesan, K., & Rahayu, S. B. (2024). Blockchain security enhancement: an approach towards hybrid consensus algorithms and machine learning techniques. Scientific Reports, 14(1), 1149.
- Karthikeyan, M., Manimegalai, D., & RajaGopal, K. (2024). Firefly algorithm based WSN-IoT security enhancement with machine learning for intrusion detection. Scientific Reports, 14(1), 231.
- Moundounga, A. R. A., & Satori, H. (2024). Stochastic Machine Learning Based Attacks Detection System in Wireless Sensor Networks. Journal of Network and Systems Management, 32(1), 17.
- Arunkumar, K. (2024). A HSEERP—Hierarchical secured energy efficient routing protocol for wireless sensor networks. Peer-to-Peer Networking and Applications, 17(1), 163-175.
- He, S., Li, Q., Khishe, M., Salih Mohammed, A., Mohammadi, H., & Mohammadi, M. (2024). The optimization of nodes clustering and multi-hop routing protocol using hierarchical chimp optimization for sustainable energy efficient underwater wireless sensor networks. Wireless Networks, 30(1), 233-252.
- Ali, A., Ali, A., Masud, F., Bashir, M. K., Zahid, A. H., Mustafa, G., & Ali, Z. (2024). Enhanced Fuzzy Logic Zone Stable Election Protocol for Cluster Head Election (E-FLZSEPFCH) and Multipath Routing in wireless sensor networks. Ain Shams Engineering Journal, 15(2), 102356.
- Goud, B. H., & Anitha, R. (2024). RAFT to Improve Failure Recovery in Wireless Sensor Networks. International Journal of Intelligent Systems and Applications in Engineering, 12(1s), 222-227.
- Xue, X., Shanmugam, R., Palanisamy, S., Khalaf, O. I., Selvaraj, D., & Abdulsahib, G. M. (2023). A hybrid cross layer with harris-hawk-optimization-based efficient routing for wireless sensor networks. Symmetry, 15(2), 438.
- Suganyadevi, K., Nandhalal, V., Palanisamy, S., & Dhanasekaran, S. (2022, October). Data security and safety services using modified timed efficient stream loss-tolerant authentication in diverse models of VANET. In 2022 International Conference on Edge Computing and Applications (ICECAA) (pp. 417-422). IEEE.
- R. Ramakrishnan, M. A. Mohammed, M. A. Mohammed, V. A. Mohammed, J. Logeshwaran and M. S, “An innovation prediction of DNA damage of melanoma skin cancer patients using deep learning,” 2023 14th International Conference on Computing Communication and Networking Technologies (ICCCNT), Delhi, India, 2023, pp. 1-7
- M. A. Mohammed, V. A. Mohammed, R. Ramakrishnan, M. A. Mohammed, J. Logeshwaran and M. S, “The three dimensional dosimetry imaging for automated eye cancer classification using transfer learning model,” 2023 14th International Conference on Computing Communication and Networking Technologies (ICCCNT), Delhi, India, 2023, pp. 1-6
- K. R. K. Yesodha, A. Jagadeesan and J. Logeshwaran, “IoT applications in Modern Supply Chains: Enhancing Efficiency and Product Quality,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 366-371.
- V. A. K. Gorantla, S. K. Sriramulugari, A. H. Mewada and J. Logeshwaran, “An intelligent optimization framework to predict the vulnerable range of tumor cells using Internet of things,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 359-365.
- T. Marimuthu, V. A. Rajan, G. V. Londhe and J. Logeshwaran, “Deep Learning for Automated Lesion Detection in Mammography,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 383-388.
- S. P. Yadav, S. Zaidi, C. D. S. Nascimento, V. H. C. de Albuquerque and S. S. Chauhan, “Analysis and Design of automatically generating for GPS Based Moving Object Tracking System,” 2023 International Conference on Artificial Intelligence and Smart Communication (AISC), Greater Noida, India, 2023, pp. 1-5, doi: 10.1109/AISC56616.2023.10085180.
- Yadav, S. P., & Yadav, S. (2019). Fusion of Medical Images using a Wavelet Methodology: A Survey. In IEIE Transactions on Smart Processing & Computing (Vol. 8, Issue 4, pp. 265–271). The Institute of Electronics Engineers of Korea. https://doi.org/10.5573/ieiespc.2019.8.4.265
- Yadav, S. P., & Yadav, S. (2018). Fusion of Medical Images in Wavelet Domain: A Discrete Mathematical Model. In Ingeniería Solidaria (Vol. 14, Issue 25, pp. 1–11). Universidad Cooperativa de Colombia- UCC. https://doi.org/10.16925/.v14i0.2236
