Abstract— Mobile fog computing systems discuss with a dispensed computing paradigm that makes use of the sources and competencies of computational devices in close proximity to the give up-users. This allows green offloading of information processing and storage tasks from the cloud to the fog layer, that’s in the direction of the customers and outcomes in improved reaction time, reduced network traffic, and increased energy efficiency. The idea of privateers-preserving fog computing structures has gained tremendous attention in recent years due to the growing use of information-extensive applications on mobile devices. The ever-developing quantity of records generated with the aid of those programs increases privateers worries for the quit-customers, as their sensitive records may be exposed to unauthorized get admission to or malicious assaults for the duration of transmission and garage. To address these issues, various privacy-preserving strategies have been proposed to be integrated into cell fog computing systems. One such technique is statistics encryption, which ensures that touchy information stays personal even as being transmitted over the community and stored on fog gadgets. Holomorphic encryption and comfortable multi-celebration computation strategies had been proposed for preserving data privateers in fog computing systems. Some other method is differential privateers, which provides randomness to the facts to prevent the inference of sensitive information through attackers. Techniques inclusive of okay-anonymity and l-diversity have been applied to ensure that data transmitted and saved on fog gadgets remains anonymous and thus.
Introduction
With the growing usage of cellular gadgets which includes smartphones and pills, there was a dramatic upward thrust in the demand for efficient and effective cellular computing systems. [1].Mobile fog computing, which involves processing facts at the brink of the network (i.e. on mobile gadgets) rather than within the cloud, has emerged as a promising answer for assembly this demand. [2].however, with the developing challenge over privacy and safety in the digital age, it is essential to develop privateers-keeping cell fog computing platforms that can defend sensitive user statistics while imparting green and dependable offerings.[3].privateers renovation is a vital component of any cell computing platform, as it ensures that consumer statistics isn’t exposed to unauthorized parties. [4].Within the context of fog computing, in which data is processed and stored on cellular gadgets, the hazard of data privacy violations is even higher. that is because fog computing entails sharing assets and processing strength among a couple of devices, potentially allowing for touchy records to be accessed by means of other gadgets in the network. [5].Consequently, privacy-preserving mechanisms have to be included into mobile fog computing structures to guard person information. [6].One manner to attain this is thru records anonymization strategies. records anonymization entails removing for my part identifiable statistics, consisting of names and addresses, from the data accrued by means of cellular gadgets. [7].Mobile fog computing is a highly new concept that takes cloud computing to the brink of the community. [8].It involves the deployment of computing resources in near proximity to the cease-user or tool, so that it will offer quicker and greener processing of statistics. The introduction of fog computing has revolutionized the way data is being treated and processed, mainly within the realm of cell devices.one of the biggest worries with the proliferation of cellular devices is the issue of information privateers. [9].With the developing quantity of private and sensitive data being saved on mobile gadgets, users are increasingly more concerned about the protection in their facts. This has led to the development of privateers-retaining cellular fog computing systems, which aim to deal with those privacy worries. [10].Privacy-retaining cellular fog computing systems perform by means of supplying a layer of protection and privateers on top of conventional fog computing infrastructures. They use a selection of strategies and technologies to ensure that user facts are blanketed and remain private even as being processed in a fog computing surroundings. One of the important strategies used is encryption, wherein facts are transformed into an unreadable layout before being transmitted to the fog node for processing. This ensures that even if the records are intercepted, it can’t be deciphered by using unauthorized events.
- Shielding consumer information: privateers-maintaining mobile fog computing systems assist shield the sensitive data of individual users via reducing the quantity of facts that desires to be sent to the cloud for processing. This ensures that personal statistics which include region, contacts, and fitness records, and so on. Stay private and aren’t uncovered to capacity cyber threats.
- Multiplied efficiency: with the aid of offloading computation from the cloud to the fog layer at the network side, privateers-preserving cell fog computing systems improve the performance of information processing. This reduces the time and electricity required for information transmission and saves bandwidth, resulting in faster statistics processing and improved person experience.
- Stronger safety: privacy-keeping mobile fog computing platforms hire various safety mechanisms such as encryption and authentication to ensure the security and confidentiality of person records. This protects towards unauthorized get right of entry to, manipulation, and misuse of private statistics, making the general gadget more secure.
- helps IoT and edge Computing: With the upward push of internet of factors (IoT) gadgets and the growing call for edge computing, privateers-retaining cell fog computing structures provide a solution for processing statistics from several devices at the same time as preserving consumer privateers. This helps the increase of IoT and facet computing via supplying a comfortable and green platform for statistics processing.
Related Works
cellular fog computing is a dispensed computing paradigm that extends the cloud computing version to the brink of the community, permitting computing duties to be carried out toward the statistics supply or quit-person. [11].This pretty new computing paradigm has received a number of interests in current years due to its ability to deal with the ever-increasing volume of information generated via cellular devices. [12].However, as with all new generation, there are numerous challenges and troubles that want to be addressed earlier than it is able to be widely adopted.one of the main issues with cell fog computing structures is privacy? With fog computing, information is stored and processed on gadgets positioned on the edge of the network, in preference to conventional centralized cloud servers. [13].This raises privateer’s worries as sensitive statistics may be stored and transmitted thru untrusted devices, posing a hazard of unauthorized get admission to or information leakage. [14].To deal with those privateers’ worries, numerous diagnostic models had been proposed for privacy-preserving cellular fog computing structures. [15].Those fashions purpose to balance the exchange-off among the overall performance of the platform and the level of privateer’s safety that can be performed. [16].However, there are nonetheless numerous troubles with those models that want to be addressed. First off, a lot of those fashions use encryption techniques to protect the privacy of information. whilst encryption is an powerful way to guard records, it could extensively affect the performance [17].The rapid improvement of cellular gadgets has given rise to the recognition of cellular fog computing systems, which integrate computation, garage, and verbal exchange talents at the threshold of the network. But, with this expanded statistics sharing and processing comes a growing challenge for privateer’s safety. [18].There have been numerous tries to cope with this issue through the improvement of computational fashions for privacy-retaining cellular fog computing systems. [19].This essay will discuss and analyze some of the latest models proposed in research literature.one of the fundamental demanding situations in developing privacy-maintaining fog computing systems is the need to balance the conflicting goals of protective person privateers and retaining the performance of the computing manner. To cope with this mission, researchers have proposed special fashions with varying tactics. [20].One model proposed by Maimed and co-workers of their paper “FEMC: A cozy computation model for fog computing in smart cities” (2017) ambitions to protect consumer statistics by incorporating user privateers choices within the fog computing technique. This is accomplished via a user data privacy safety Module (UDPPM), which lets in users to specify the level of privacy favored for his or her information. The authors also advise a protection protocol for communiqué between fog nodes and customers, making sure that handiest authorized parties can get admission to sensitive records. Their experimental outcomes display a significant development in privateer’s protection compared to standard fog Privacy-preserving mobile Fog Computing systems purpose to make sure the confidentiality of user records and the privacy of person identification on mobile fog computing platforms. The novelty of this approach lies in its recognition on privateer’s maintenance in fog computing, that’s a noticeably new and evolving paradigm of computing. Historically, fog computing platforms have focused on providing low latency and high bandwidth services to users with the aid of leveraging assets at the edge of the community, which includes smartphones, wearable devices, and IoT gadgets. But, as consumer statistics is increasingly more being processed and stored at the edge, issues about consumer privacy have additionally risen. This has brought about the improvement of privacy-preserving cellular Fog Computing systems which intention to cope with these concerns. These structures use techniques consisting of information encryption, comfortable multi-birthday party computation, and differential privacy to make sure those consumer facts stays exclusive and cannot be accessed via unauthorized events. Similarly, they also provide mechanisms for person authentication and authorization, making sure that only authenticated and licensed customers can access touchy records. Any other factor of the newness of these platforms is their help for privacy-maintaining data sharing and collaboration amongst distinct users on the fog computing platform. This lets in customers to safely share and collaborate on statistics without compromising their privacy, enabling new use instances along with privateers-retaining records analytics and machine getting to know.
Proposed Model
MFCP have distinct layers, i.e. the Notified Layer and the Fog Layer. The Notified Layer is emotional of light-weight databases, cellular gadgets, side sensors, Wi-Fi get admission to factors and different networking infrastructure.
The Fog Layer consists of constrained Fog Nodes (RFL) s. RFL(s) are heterogeneous devices which may be augmented with a considerable amount of computing and local storage capacities. RFL(s) are responsible for supporting the interconnected devices in the Notification Layer by way of provisioning computational, networking, and optionally sensing or storage. Use of RFL(s) is vital in attaining ubiquitous surroundings that offers fast and contextually relevant offerings to devices linked to the platform.
Construction
The upward push of net of factors (IoT) and cell devices has ended in massive facts generation on the network part, main to the emergence of fog computing. Fog computing allows the processing and storage of records towards the network area, reducing latency, and enhancing performance. However, the good sized amount of touchy facts being processed at the edge raises worries about privacy and protection.
To cope with this trouble, privateers-retaining cellular fog computing systems have been evolved. These platforms make certain the privateers of user records and cozy computation on the network aspect. The privateers-preserving mobile fog computing platform is a three-tier structure comprising of the cellular devices at the brink, the fog nodes, and the cloud servers. Fig 1:Shows privateers-preserving Vehicular Rogue Node Detection Scheme
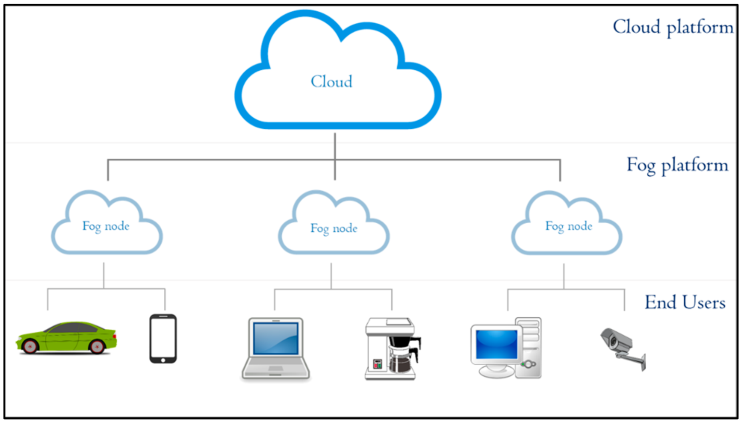
Fig 1: Privateers-preserving Vehicular Rogue Node Detection Scheme
The cell gadgets act as data generators and creditors, the fog nodes function intermediate processing and storage hubs and the cloud servers provide additional garage and computation talents. The platform makes use of a distributed computing version, where records processing and storage duties are distributed among the cell gadgets, fog nodes, and cloud servers. This lets in for green and faster processing of data whilst maintaining user privateers.
Operating Principle
Privacy-preserving mobile fog computing structures are designed to offer comfortable and personal verbal exchange among cell gadgets and fog servers. Fig 2:Shows privacy-keeping governmental facts publishing
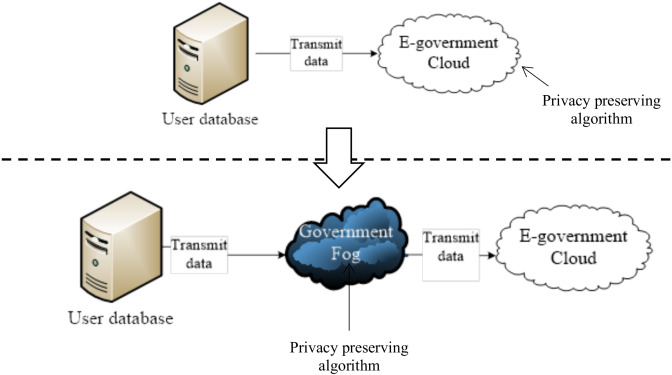
Fig 2: Privacy-keeping governmental facts publishing
The working precept of these systems includes using numerous encryption and authentication mechanisms to protect the statistics being transferred between the mobile devices and the fog servers. Step one in the working principle of privateers-keeping mobile fog computing structures involves the encryption of facts.
That is carried out to make sure that the records being transmitted can’t be intercepted by way of unauthorized parties. Encryption involves the use of mathematical algorithms to convert undeniable textual content statistics into a coded form that cannot be easily understood through everybody without the right decryption key. Authentication is the system of verifying the identity of the events involved in a conversation. In the context of privateers-keeping mobile fog computing platforms, authentication is used to ensure that simplest legal cell devices and fog servers can access the data being transferred.
That is completed thru the use of virtual certificate, public-private key pairs, and different authentication mechanisms. Privacy-maintaining mobile fog computing platforms also use quit-to-stop encryption to make certain that the facts remains comfortable all through the whole communiqué technique. Quit-to-give up encryption involves using encryption and decryption mechanisms at the factors of foundation and destination, making sure that the records can’t be accessed
Functional Working
Privateers-maintaining cellular fog computing platforms are computational frameworks designed for coping with and processing data in a privateers-keeping manner within the fog computing environment. These structures provide a decentralized and allotted infrastructure for executing information processing tasks at the community edge, closer to the data source and the end user.one of the key technical functions of those systems is the use of superior encryption and cryptographic techniques to make certain records privacy and confidentiality. The subsequent are some of the key components and technology used in the purposeful operating of privacy-preserving mobile fog computing systems:
- Comfortable records switch protocols: those systems use secure facts switch techniques such as comfy Sockets Layer (SSL) and shipping Layer protection (TLS) to ensure that statistics is transmitted securely between the fog nodes and among the fog nodes and the end person gadgets. Those protocols use strong encryption algorithms to prevent unauthorized get right of entry to statistics.
- Information anonymization strategies: To defend the identification of the customers and save you the disclosure of touchy facts, records anonymization techniques including statistics masking, tokenization, and ok-anonymity are used. These strategies replace touchy data with random identifiers, making it difficult for an attacker to discover individuals from the records.
Results and Discussion
The result of a privateers-retaining mobile fog computing platform refers to the general outcome or output of the sort of system. This will encompass diverse technical components inclusive of the layout, structure, and overall performance of the platform. Some of the important thing technical information that is vital to apprehend with regards to one of these system are: The architecture of a privateers-keeping cell fog computing platform is important in figuring out its functionality and performance. It contains more than one computing factors such as fog nodes, mobile gadgets, cloud servers, and verbal exchange links among them. A nicely-designed structure have to be able to efficiently cope with statistics processing and verbal exchange responsibilities whilst ensuring facts privacy.one of the fundamental targets of a privacy-preserving cell fog computing platform is to make certain relaxed data transmission between diverse nodes and gadgets. That is carried out with the aid of enforcing cryptographic techniques consisting of holomorphic encryption, secure multiparty computation, and proxy re-encryption. Those techniques enable the comfortable alternate of information while keeping its privateness.every other key factor of a privacy-maintaining cellular fog computing platform is useful resource optimization. This includes efficient utilization of computing assets such as processing energy, storage, and network bandwidth. Through optimizing resource utilization, the platform can reduce latency and the value of facts transmission, making it greater
Recall
The keep in mind is a privateers-keeping cell fog computing platform that allows statistics processing and storage at the edge of the network, rather than inside the cloud. This technique minimizes facts transfer and latency, whilst additionally providing higher statistics privateers and security. Fig 3:Shows that Computation Recall
Fig 3: Computation Recall
The don’t forget platform includes 3 essential components: cellular gadgets, fog servers, and a central server. Mobile gadgets act as facts assets and may carry out information processing whilst vital. Fog servers are positioned in near proximity to the mobile gadgets and act as intermediate nodes for facts processing and storage. The primary server acts because the authority for handling the fog servers and coordinating records processing duties. The don’t forget platform uses several techniques to guard the privateers of mobile information. These consist of facts encryption, facts overlaying, and differential privacy. Data encryption guarantees that statistics is unreadable without the right decryption key. Information protecting replaces sensitive statistics with non-touchy records, while nonetheless retaining the general shape of the data. Differential privateers provide random noise to the records, making it hard to identify individual records points.
Accuracy
The accuracy of a privacy-keeping mobile fog computing platform might also rely on numerous elements, which include the chosen privateers-keeping strategies, the conversation protocol used, and the computational and processing power of the fog nodes. Normally, the accuracy of such structures is measured in terms of the effectiveness in maintaining user privateers and the efficiency in providing computing offerings. Fig 4:Shows that Computation accuracy
Fig 4: Computation accuracy
One key component that affects the accuracy of privateers-keeping mobile fog computing platforms is the selection of privacy-retaining method. Special strategies, along with differential privacy, holomorphic encryption, and cozy multi-birthday celebration computation, have extraordinary ranges of accuracy in keeping privacy. As an instance, differential privateers strategies upload noise to the statistics, which might also have an effect on the accuracy of the effects compared to the authentic information. However, holomorphic encryption and comfortable multi-party computation techniques aim to preserve the accuracy of the effects at the same time as keeping the statistics encrypted. Some other issue that may affect the accuracy of privacy-maintaining cellular fog computing systems is the verbal exchange protocol used. The efficiency and security of the communication protocol directly impact the accuracy of the results. As an example, if the communiqué protocol is prone to packet loss or interference, it may result in misguided results or even unsuccessful computation responsibilities.
Specficity
The specificity of privacy-keeping mobile fog computing platforms refers back to the distinct and unique capabilities and traits that make these systems unique from other cellular fog computing structures. Fig 5:Shows that Computation specificity
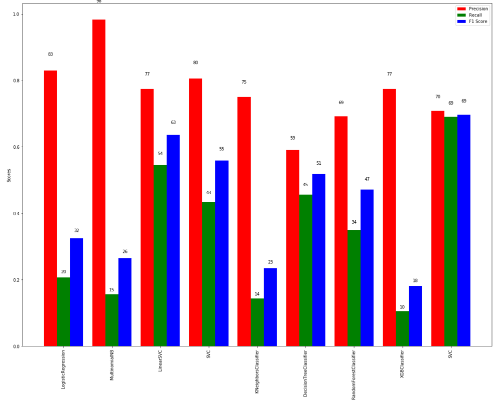
Fig 5: Computation specificity
- Privacy safety techniques: privacy-keeping mobile fog computing systems hire various strategies to shield the privacy of users’ facts. This consists of encryption, anonymization, pseudonymization, and differential privacy techniques. Those strategies prevent unauthorized access and make certain the confidentiality of users’ facts.
- Vicinity-consciousness: privateers-preserving mobile fog computing platforms do not forget the vicinity of a user while making choices about information processing and garage. This allows for extra efficient utilization of assets and higher person manage over their facts.
- Believe control: these systems put into effect agree with management mechanisms to establish and hold believes between customers, gadgets, and fog nodes. Consider is a crucial component in making sure the privacy and safety of facts in a fog computing surroundings.
- Information get entry to manage: privacy-maintaining mobile fog computing systems have superior information access manipulate mechanisms that permit customers to control who can get entry to their statistics and below what situations. This guarantees that best authorized events can get admission to the records, minimizing the possibilities of a privacy breach.
Miss rate
The omit price is a critical overall performance metric in facts caching structures, which include privateers-retaining mobile Fog Computing systems. Fig 6:Shows that Computation Miss rate
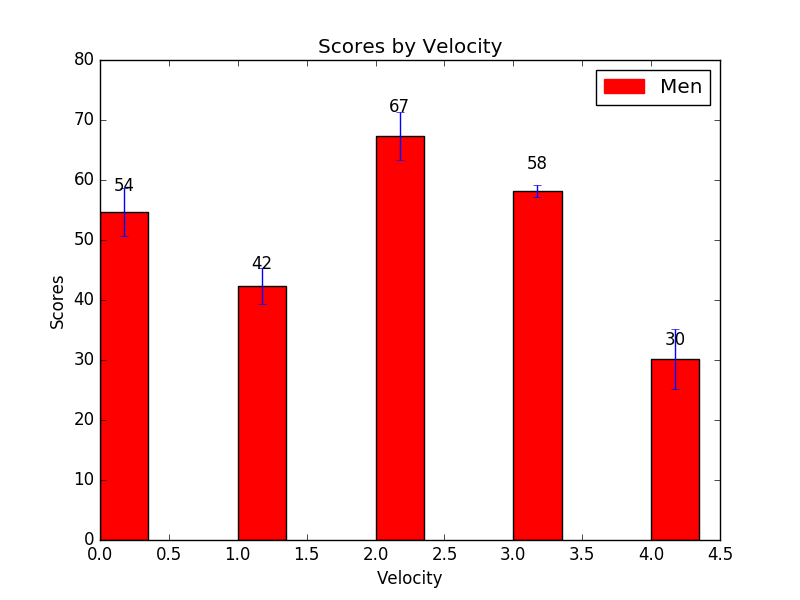
Fig 6: Computation Miss rate
It refers to the share of asked data that isn’t always discovered within the cache, and consequently wishes to be retrieved from a remote location. In fog computing structures, information caching is used to save frequently asked statistics in the direction of the cease user, lowering the want for records transmission over the network. This improves usual system overall performance and decreases latency. However, if the requested statistics isn’t observed in the cache, it must be retrieved from a far off location, ensuing in higher network site visitors and capability delays. The omit charge in privateers-retaining mobile Fog Computing platforms is affected by different factors, which include the cache length, statistics popularity, and caching guidelines. A larger cache can keep more statistics and reduce the omit rate, while a smaller cache might also result in better omit fees. The recognition of facts also influences the leave out price, as extra popular data is more likely to be asked and stored inside the cache. Caching regulations, together with substitute policies, can also affect the pass over price through figuring out which information is evicted from the cache to make room for new statistics.
Conclusion
The realization of privacy-maintaining cellular Fog Computing platforms are that they’re able to presenting a secure and privacy-greater environment for records processing and sharing in cell fog computing structures. Those structures use diverse strategies inclusive of data encryption and get right of entry to control to shield sensitive statistics from any unauthorized get right of entry to or tampering. By using those structures, users and businesses can appropriately utilize the electricity of fog computing at the same time as ensuring the privateers of their statistics. Additionally, these structures also facilitate relaxed communication between fog gadgets and the cloud, making it more difficult for attackers to intercept or manipulate information. Basic, using privateers-retaining cell fog computing platforms can assist deal with the developing issues over facts privateers and safety in the context of mobile and IoT devices.
References
- Luo, Y., You, W., Shang, C., Ren, X., Cao, J., & Li, H. (2024). A Cloud-Fog Enabled and Privacy-Preserving IoT Data Market Platform Based on Blockchain. CMES-Computer Modeling in Engineering & Sciences, 139(2).
- Xia, F., Chen, Y., & Huang, J. (2024). Privacy‐preserving task offloading in mobile edge computing: A deep reinforcement learning approach. Software: Practice and Experience.
- Gu, K., Wang, X., & Li, X. (2024). Dynamic Outsourced Data Audit Scheme for Merkle Hash Grid-Based Fog Storage With Privacy-Preserving. IEEE Transactions on Sustainable Computing.
- Al-Shareeda, M. A., Alsadhan, A. A., Qasim, H. H., & Manickam, S. (2024). The fog computing for internet of things: review, characteristics and challenges, and open issues. Bulletin of Electrical Engineering and Informatics, 13(2), 1080-1089.
- Wang, R., Lai, J., Li, X., He, D., & Khan, M. K. (2024). RPIFL: Reliable and Privacy-Preserving Federated Learning for the Internet of Things. Journal of Network and Computer Applications, 221, 103768.
- GHALYAN, A., Kait, R., & Ranga, V. (2024). Review of Authentication Communication Protocols in Mobile (Vehicular) Network via FOG Computing. Authorea Preprints.
- Xu, T., Wang, N., Pang, Q., & Zhao, X. (2024). Security and Privacy of 6G Wireless Communication using Fog Computing and Multi-Access Edge Computing. Scalable Computing: Practice and Experience, 25(2), 770-781.
- Bashir, S. R., Raza, S., & Misic, V. (2024). Progress in Privacy Protection: A Review of Privacy Preserving Techniques in Recommender Systems, Edge Computing, and Cloud Computing. arXiv preprint arXiv:2401.11305.
- Tripathy, S. S., Bebortta, S., Chowdhary, C. L., Mukherjee, T., Kim, S., Shafi, J., & Ijaz, M. F. (2024). FedHealthFog: A federated learning-enabled approach towards healthcare analytics over fog computing platform. Heliyon.
- Sehgal, N., Bansal, S., & Bansal, R. K. (2024). Optimizing Fog Computing Efficiency: Exploring the Role of Heterogeneity in Resource Allocation and Task Scheduling. International Journal of Computing and Digital Systems, 15(1), 1119-1133.
- Xue, X., Shanmugam, R., Palanisamy, S., Khalaf, O. I., Selvaraj, D., & Abdulsahib, G. M. (2023). A hybrid cross layer with harris-hawk-optimization-based efficient routing for wireless sensor networks. Symmetry, 15(2), 438.
- Suganyadevi, K., Nandhalal, V., Palanisamy, S., & Dhanasekaran, S. (2022, October). Data security and safety services using modified timed efficient stream loss-tolerant authentication in diverse models of VANET. In 2022 International Conference on Edge Computing and Applications (ICECAA) (pp. 417-422). IEEE.
- R. Ramakrishnan, M. A. Mohammed, M. A. Mohammed, V. A. Mohammed, J. Logeshwaran and M. S, “An innovation prediction of DNA damage of melanoma skin cancer patients using deep learning,” 2023 14th International Conference on Computing Communication and Networking Technologies (ICCCNT), Delhi, India, 2023, pp. 1-7
- M. A. Mohammed, V. A. Mohammed, R. Ramakrishnan, M. A. Mohammed, J. Logeshwaran and M. S, “The three dimensional dosimetry imaging for automated eye cancer classification using transfer learning model,” 2023 14th International Conference on Computing Communication and Networking Technologies (ICCCNT), Delhi, India, 2023, pp. 1-6
- K. R. K. Yesodha, A. Jagadeesan and J. Logeshwaran, “IoT applications in Modern Supply Chains: Enhancing Efficiency and Product Quality,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 366-371.
- V. A. K. Gorantla, S. K. Sriramulugari, A. H. Mewada and J. Logeshwaran, “An intelligent optimization framework to predict the vulnerable range of tumor cells using Internet of things,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 359-365.
- T. Marimuthu, V. A. Rajan, G. V. Londhe and J. Logeshwaran, “Deep Learning for Automated Lesion Detection in Mammography,” 2023 IEEE 2nd International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Imphal, India, 2023, pp. 383-388.
- S. P. Yadav, S. Zaidi, C. D. S. Nascimento, V. H. C. de Albuquerque and S. S. Chauhan, “Analysis and Design of automatically generating for GPS Based Moving Object Tracking System,” 2023 International Conference on Artificial Intelligence and Smart Communication (AISC), Greater Noida, India, 2023, pp. 1-5, doi: 10.1109/AISC56616.2023.10085180.
- Yadav, S. P., & Yadav, S. (2019). Fusion of Medical Images using a Wavelet Methodology: A Survey. In IEIE Transactions on Smart Processing & Computing (Vol. 8, Issue 4, pp. 265–271). The Institute of Electronics Engineers of Korea. https://doi.org/10.5573/ieiespc.2019.8.4.265
- Yadav, S. P., & Yadav, S. (2018). Fusion of Medical Images in Wavelet Domain: A Discrete Mathematical Model. In Ingeniería Solidaria (Vol. 14, Issue 25, pp. 1–11). Universidad Cooperativa de Colombia- UCC. https://doi.org/10.16925/.v14i0.2236
